In today’s increasingly complex digital world, old-fashioned security methods that rely on trusting users and devices within the network perimeter are no longer enough. The Zero Trust model offers a new way of thinking about security. It challenges current security assumptions and requires a big change in how we protect our digital resources.
1. Zero Trust Model
The zero-trust concept is based on “never trust, always verify.” All access requests are carefully checked to ensure that no entity, whether inside or outside the network, is given unrestricted access. This approach assumes that potential threats can come from internal and external sources. Therefore, it promotes strict scrutiny of all access requests and regular verification procedures.
Zero Trust is a comprehensive security approach that covers all aspects of your digital infrastructure, including identities, endpoints, networks, data, applications, and systems. Creating a robust security architecture requires seamless integration across all these elements. The Zero Trust Architecture components are :
- Identity
- Endpoints
- Infrastructure
- Network
- Applications
- Data
- Security Policy (Enforcement).
- Security Policy Optimisation
- Threat protection
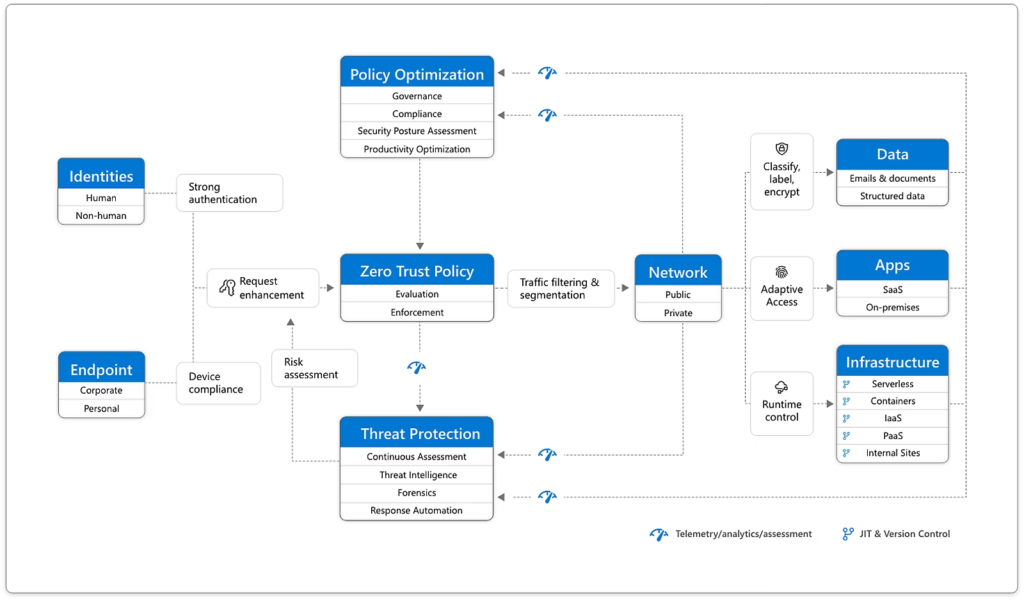
This blog post will delve into the Zero Trust model’s intricacies, exploring how to leverage Azure Networking Services’ comprehensive security features to implement a Zero Trust security model to enhance protection for cloud-based resources and data.
2. Azure Networking Services
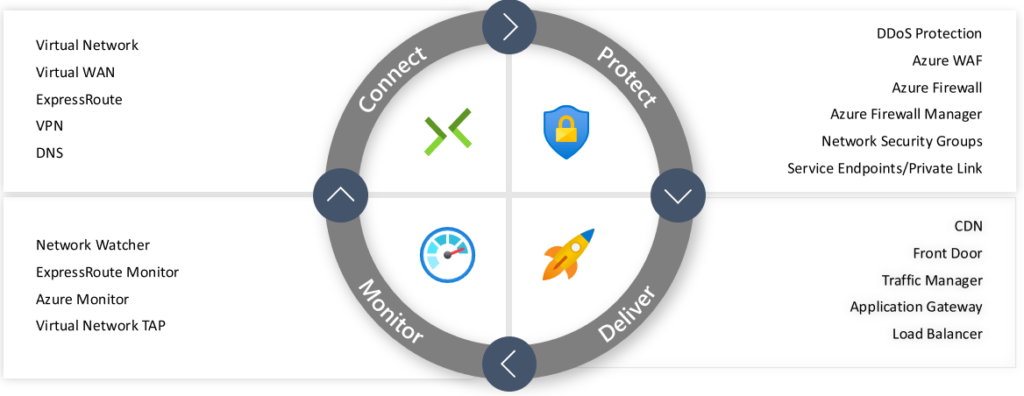
Azure Networking Services are categorized into various capabilities: connect, protect, monitor, and deliver. The picture below shows a breakdown of Azure networking services within these categories.
2.1 Azure DDoS
Azure DDoS Protection is a service designed to safeguard applications and resources hosted on Azure from Distributed Denial of Service (DDoS) attacks. It safeguards any internet-facing resource within a virtual network. It is easy to enable on new and existing virtual networks and does not require application or resource modifications. This protection operates at network layers 3 and 4. For layer 7 web application protection, you need to implement a WAF for additional application layer security.
Azure DDoS Protection supports two tier types: IP Protection and Network Protection. When you configure Azure DDoS Protection, the Azure portal configures the tier during the workflow.
- 2.1.1 Network Protection
- Azure DDoS Network Protection is designed to shield Azure-hosted resources from large-scale network attacks that have the potential to overwhelm services and lead to operational disruptions.
- This service protects 100 public IP resources by analysing traffic intelligently.
- It is easy to set up and deploy through the Azure portal, as it is natively integrated.
- DDoS Network Protection automatically defends all resources on a virtual network against potential threats.
- It monitors network traffic for DDoS attacks and takes action to stop them when detected.
- Detailed reports are provided every five minutes during an attack, and a summary report is available once the attack is over.
- It supports integrating mitigation logs with Microsoft Defender for Cloud, Microsoft Sentinel, or an offline security information and event management (SIEM) system, enabling near real-time monitoring and rapid response during an attack.
- Azure Monitor collects monitoring data from DDoS Network Protection to provide access to summarized attack metrics.
- 2.1.2 IP Protection
- DDoS IP Protection contains the same core engineering features as DDoS Network Protection but differs in the following value-added services:
- DoS rapid response support
- Cost protection
- Discounts on WAF.
- DDoS IP Protection contains the same core engineering features as DDoS Network Protection but differs in the following value-added services:
By leveraging Azure DDoS Protection, organisations can enhance their resilience against DDoS attacks, ensuring their applications and services remain available and performant even under attack. Azure DDoS Network Protection is crucial for maintaining the availability and reliability of your applications and services hosted on Azure. By integrating these protections into your network architecture, you can better guard against the growing threat of DDoS attacks.
For more detailed information about this service, please visit my previous blog about Azure DDoS.
2.2 Azure Firewall
In the Zero Trust Security Model, a firewall is critical for enhancing security and ensuring that applications or services are available to the end user within the agreed SLAs. By inspecting every network traffic and controlling which data can enter or exit the environment, a firewall helps mitigate the risk of cyber-attacks and unauthorized access to sensitive information.
Additionally, a firewall can enforce security policies, monitor network traffic, and act as a barrier against potential threats, enhancing the overall security posture of the environment. The Zero Trust approach recommends filtering traffic between network levels, hosts, and applications. Azure provides various firewalling services that address host, Application, and network-level security needs.
2.2.1 Firewalling Services at the Host Level
Azure Network Security Group (NSG): NSGs control inbound and outbound traffic to and from Azure resources at the network interface or subnet level. The more relevant application of NSG in Zero Trust networks is associated with a specific VM (such as assigning an NSG to a VM NIC). It supports filtering policy per VM, making the VM a participant in its security. It aims to ensure that every VM filters its network traffic rather than delegating all firewalls to a centralized firewall.
While host firewalling can be implemented at the guest OS level, Azure NSG safeguards against a compromised VM. An attacker who gains access to the VM and elevates its privileges could remove the on-host firewall. NSG is implemented outside of the VM, isolating host-level filtering, which provides strong guarantees against attacks on the firewalling system.
Another service is Azure Application Security Groups (ASGs), an Azure feature that simplifies network security management by allowing you to group and manage network security policies based on applications rather than IP addresses. They provide a way to apply network security rules more intuitively and scalable.
ASGs let you group resources with similar security needs and apply security rules to these groups instead of managing rules for individual IP addresses or network interfaces. ASGs make it easier to manage dynamic applications where resources frequently change. As resources are added to or removed from ASGs, the security policies automatically apply to the appropriate resources. Using ASGs, you can efficiently manage security at scale, especially in large or complex environments with numerous resources. Create ASGs to group VMs, virtual machine scale sets, or other network interfaces with common security requirements.
2.2.2 Firewalling Services at the Network Level
Implementing firewalling at the virtual network or subnet level is crucial for enhancing security. This approach safeguards a substantial part of the infrastructure against unauthorized traffic and potential internet-based attacks and protects east-west traffic to contain the impact of potential security breaches.
Azure Firewall is a native network security service designed for firewalling. When firewalls are used with NSG (Network Security Group), these services establish essential safeguards within zero-trust networks. Azure Firewall enforces global rules and broad host policies, while NSG defines policies in more detail. This clear differentiation between perimeter and host filtering can streamline the management of firewall policies.
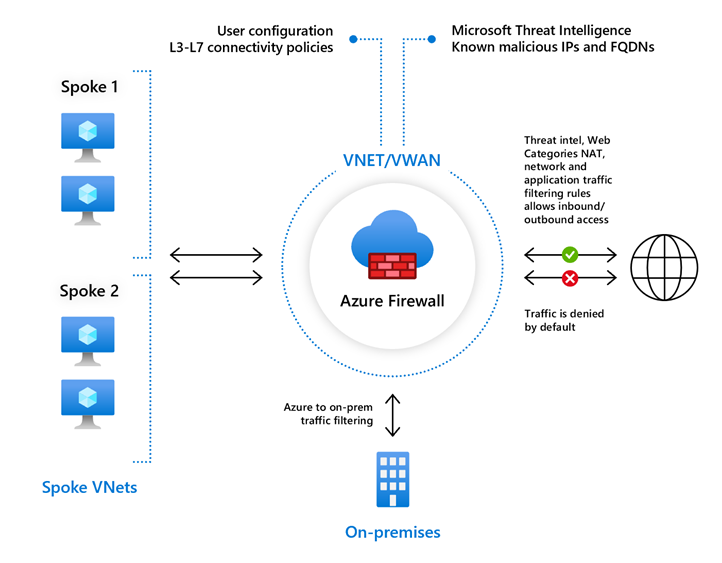
The Azure Firewall service has different SKUs available:
- Azure Firewall Premium
- Azure Firewall Standard
- Azure Firewall Basic
For more detailed information about this service, please visit my previous blog about Azure Firewall.
Another service is Azure Firewall Manager provides centralized management for Azure Firewall and Azure Firewall Policy across multiple Azure regions and subscriptions. It streamlines the deployment, configuration, and monitoring of Azure Firewall instances, enhancing the overall security posture of your network infrastructure. It easily assigns policies to Azure Firewall instances or specific virtual networks, streamlining rule management. This allows the management of multiple Azure Firewall instances from a single, centralized location and simplifies the administration of security policies and rules.
For more detailed information about this service, please visit my previous blog about Azure Firewall Manager.
2.2.3 Firewalling Services at the Application Level
Azure Web Application Firewall is a cloud-native service that protects web apps from common web-hacking techniques such as SQL injection and cross-site scripting. It can be deployed with Microsoft’s Azure Application Gateway, Front Door, and Content Delivery Network (CDN) services. WAF on Azure CDN is currently under public preview and has customized features for each specific service.
For more detailed information about this service, please visit my previous blog about Azure WAF.
2.3 Azure Private Endpoint
Azure Private Endpoint is an essential feature in Azure that offers secure, private connectivity to Azure services over the Azure backbone network. With Azure Private Endpoints, you can connect to Azure services using a private IP address within your Virtual Network (VNet). This setup ensures that traffic between your VNet and the Azure service does not travel over the public internet, which reduces the risk of potential security threats. By using Private Endpoints, the Azure service is only accessible within your VNet, effectively reducing the attack surface by preventing direct access from the public internet. Private endpoints can provide lower latency and more consistent application performance by keeping traffic within Azure’s network.
Furthermore, Azure Private Link Service is crucial in connecting your services to other VNets, providing a private and secure environment for your operations.
For more detailed information about this service, please visit my previous blog about Azure Private Endpoint.
2.4 Azure Defender for Cloud
Azure Defender for Cloud (formerly known as Azure Security Center) is a robust cloud security solution offered by Microsoft Azure. It is designed to safeguard your cloud resources from various security threats. This comprehensive solution provides various capabilities to enhance your security posture, identify vulnerabilities, and effectively respond to potential threats.
This service serves as a centralized platform for monitoring the security of your Azure environment, encompassing virtual machines, databases, containers, and even resources from other cloud providers such as AWS and GCP. It empowers you to establish and enforce security policies across your Azure resources, on-premises environments, and other cloud providers. Notable features include threat protection, compliance management, vulnerability management, and endpoint protection.
This solution helps the organisation identify security compliance across its infrastructure, which might be vulnerable to security threats.
For more detailed information about this service, please visit my previous blog about Defender for Cloud.
2.5 Microsoft Sentinel
Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) solution pivotal for deploying a Zero-Trust security model. Zero Trust, a security framework, operates on the assumption of no inherent trust within the network and enforces stringent access controls and continuous verification of users, devices, and applications.
This platform consolidates data from diverse sources such as users, devices, applications, and infrastructure, presenting a unified perspective of security events across the entire environment. It delivers insights into all activities and potential network threats, irrespective of origin, aligning with the zero-trust principle of comprehensive verification.
Microsoft Sentinel employs automated playbooks to address incidents based on predefined rules and workflows. This results in swift threat containment and mitigation, reducing the need for manual intervention. The system’s efficiency in identifying and addressing threats will give you confidence in its ability to keep your network secure.
Final thoughts:
Organisations can adopt the zero-trust security model using the Azure services mentioned above. Microsoft is adding more security services for the customer, and Copilot for Security is another service for organisations. Some organisations would have invested in a tool that would be extended to Azure. For example, some customers use Palo or Cisco firewalls instead of the Azure Firewall. Azure supports third-party firewall deployment. Zero Trust model is a continuous process for security experts, but the initial steps involve taking proactive measures and making consistent, incremental enhancements. The article outlines various Azure security services and their role in facilitating the zero-trust approach for all organisations.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

