Welcome to this blog post, which focuses on the steps required to enable Microsoft Defender for Endpoint (MDE) on server operating systems. For the prerequisites and other essential information, please visit the first part of this blog post in this series.
Azure Servers – Deployment
To onboard Microsoft Defender for Endpoint (MDE) onto servers running on Azure-based virtual machines, we must enable the Defender for Server plan in Microsoft Defender for Cloud (MDC). This integration helps eliminate the need for the now-retired Log Analytics agent (MMA).
Defender for endpoint unified solution is deployed to Azure Windows servers automatically. For Linux servers, it must be enabled at the subscription level under the Defender for servers plan on MDC.
To enable the Defender for Server plan for Azure servers, follow these steps:
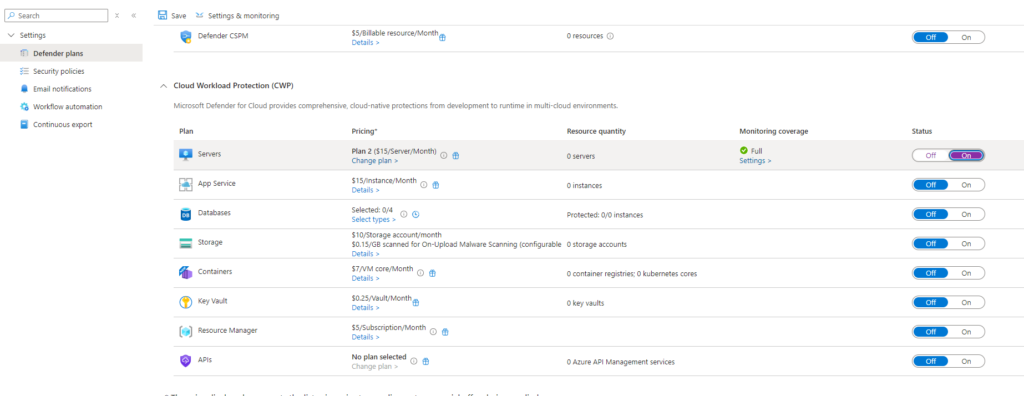
After enabling Defender for Servers on your subscriptions, this coverage does not automatically extend to an attached Azure Log Analytics workspace. You must enable Defender for Servers, specifically at the Azure Log Analytics workspace level. To do this, follow these steps:
- Sign in to the Azure portal and select the Microsoft Defender for Cloud service.
- Navigate to the environment settings in Microsoft Defender for Cloud.
- Choose the desired Azure Log Analytics workspace.
- Toggle the server plan to “On.”
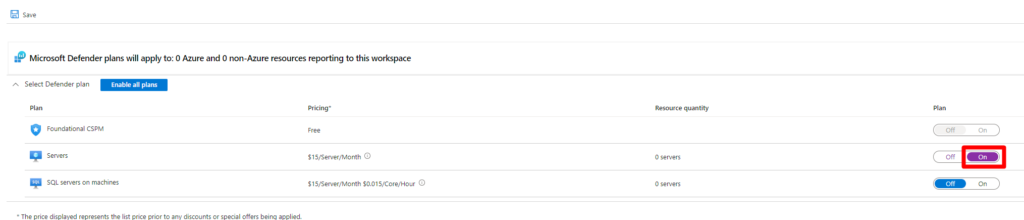
Once the settings mentioned above are activated, Microsoft Defender for Endpoint (MDE) will be fully operational across all virtual machines within the specified subscriptions. If you need to enable this feature for specific resources rather than globally, you have two practical options at your disposal:
- REST API: This method allows for programmatically enabling MDE at a granular level, giving you flexibility in managing MDE for the required resource settings.
- PowerShell Script: This option allows you to use a script to easily enable MDE on desired resources, making deployment and management straightforward.
Both methods provide a means to tailor the security capabilities of Microsoft Defender according to your specific needs.
To enforce the onboarding of MDE using Azure policy. Azure has a built-in Configure Azure Defender for Servers to be enabled policy definition for your deployment.
AWS & GCP Cloud Servers – Deployment
Onboarding an AWS or GCP account to Microsoft Defender for Endpoint involves several steps to ensure proper integration and security management. Here’s a high-level overview of the process:
- Pre-requisites
- Azure Subscription with MDC enabled and contributor-level access permission.
- AWS account or GCP project with required access permission.
- Configure the Defender for endpoint
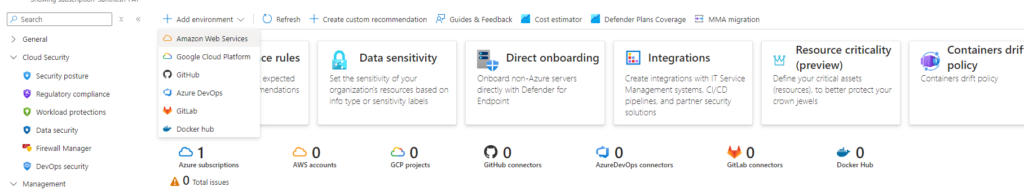
- Under MDC service, in the environment settings, click Add Environment to add AWS or GCP.
- Please complete all required details to connect your other cloud (AWS or GCP) to MDC. In the next window, select the server plan, which will provide MDE for the servers.
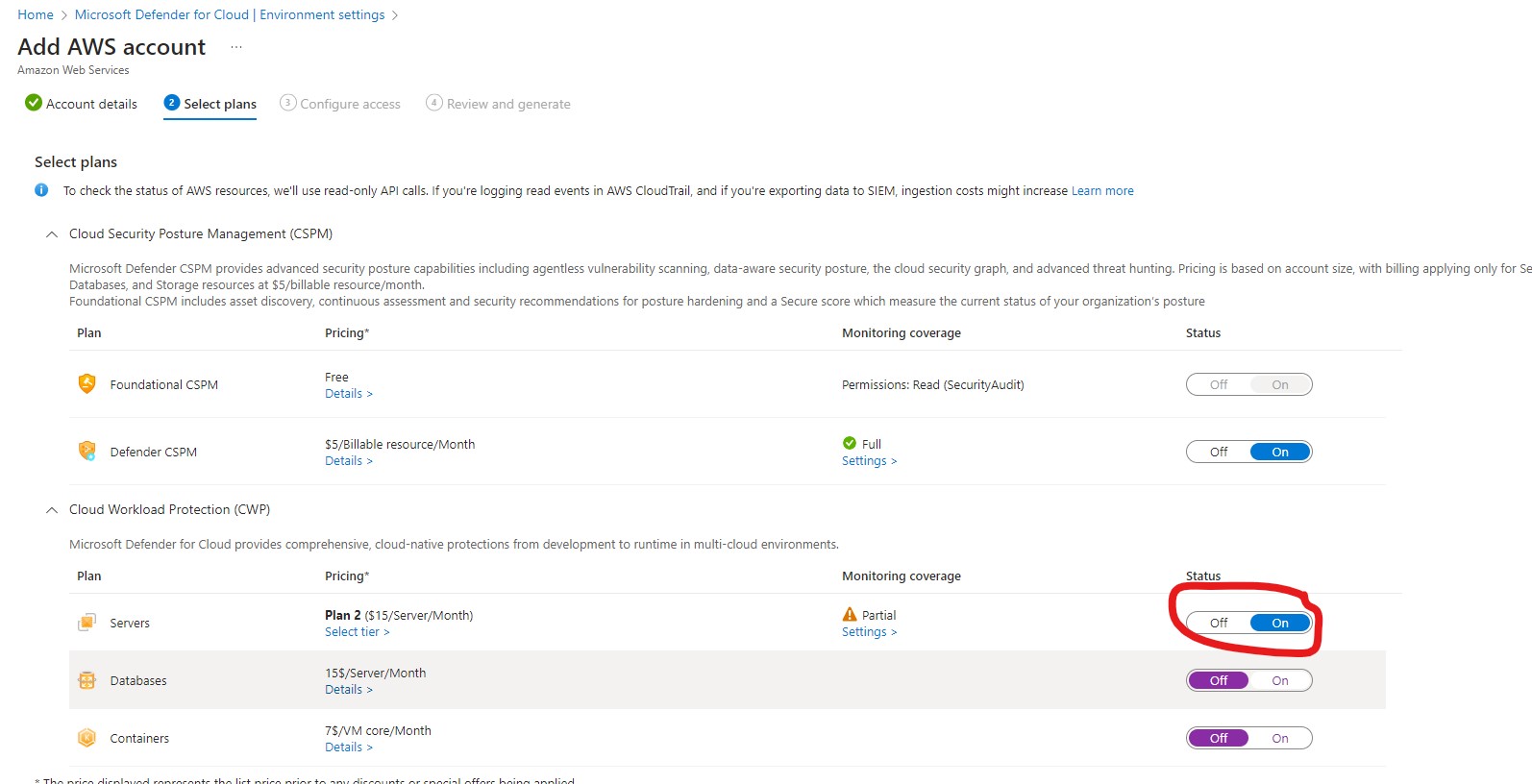
- A template has been generated based on the plans selected in the previous sections to configure access on AWS or GCP cloud. We need to execute these templates. Custom role(s) will be created to facilitate the automatic onboarding of the AWS management account and future accounts.
- We can select the least privileged access on the other cloud. These templates are AWS cloud formation, or GCP terraform.
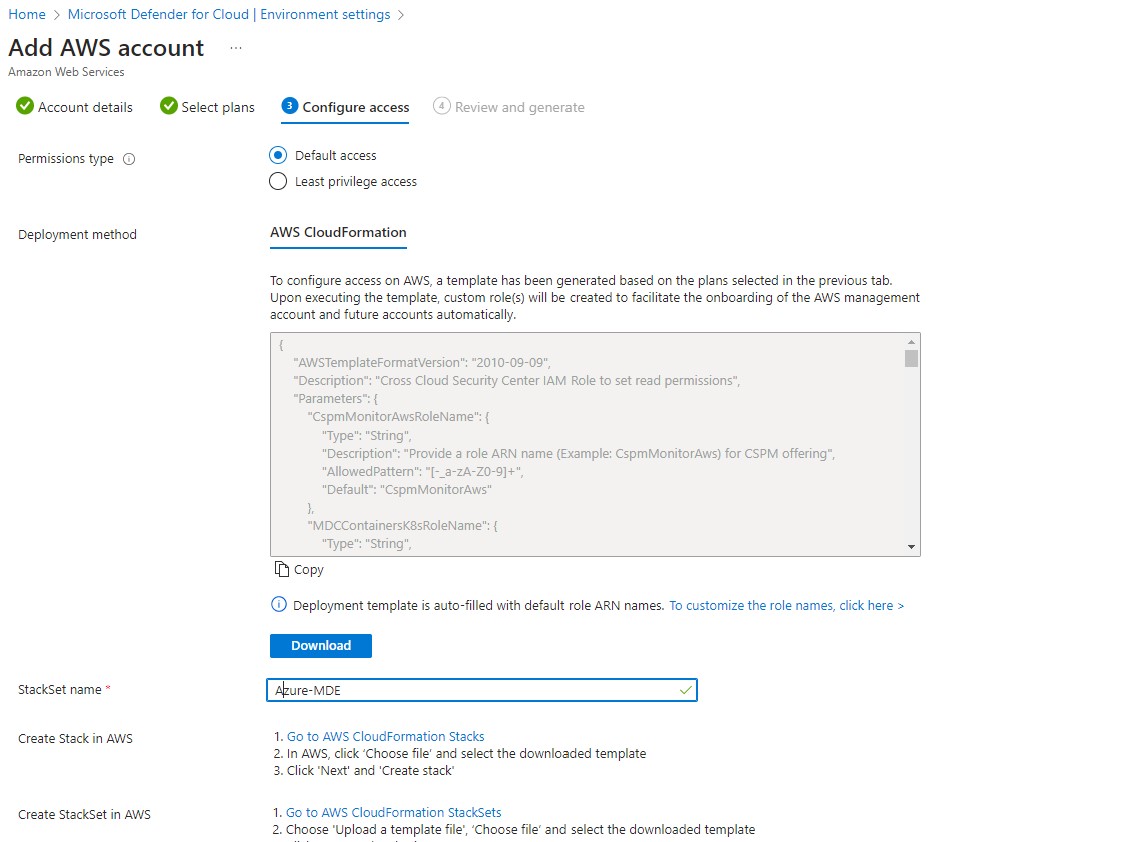
- The template will have an IAM role and be part of EC2 with an IAM profile that allows MDC to access, manage and provide the relevant security features.
- The connectivity required for non-Azure cloud VMs to Azure public endpoints can be whitelisted with required public endpoints on the firewall for secure access from other cloud-based servers.
- Under MDC service, in the environment settings, click Add Environment to add AWS or GCP.
Azure Arc Cloud Servers – Deployment
Onboarding the MDE with non-Azure VMs can be performed with two options:
- Connect machines with Azure Arc
- To leverage Azure’s benefits, it’s essential to have an Azure Arc agent installed for the on-premise servers. Once onboarded into a subscription, Azure Arc-enabled servers offer enhanced functionalities.
- After the resources are in Azure via Azure Arc, we need to enable the MDE by enabling the Defender for the server plan, as mentioned in the Azure deployment.
- These capabilities include implementing guest configuration policies directly on the machines and streamlining deployment processes with various Azure services.
- The connectivity required for Azure arc on-premise VMs to Azure public endpoints can be turned into an Azure private link and used with an express route for secure access from on-premise servers.
- Connect machines with Defender for endpoint.
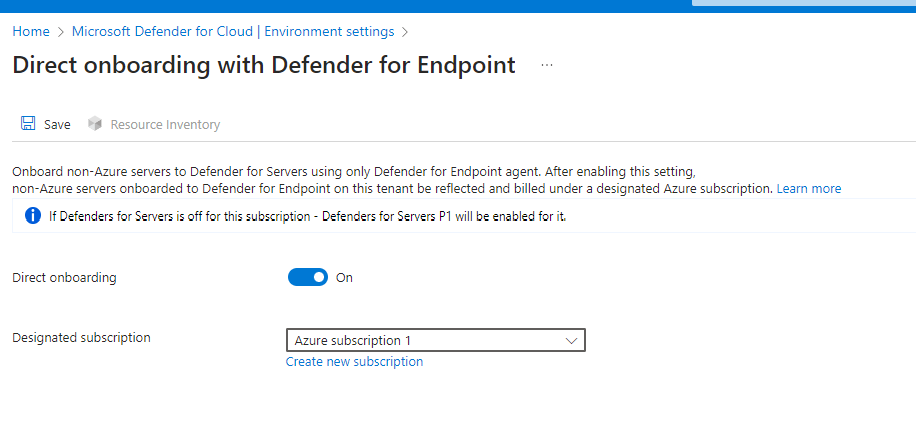
- Deploying the Defender for Endpoint agent on your on-premises Windows and Linux servers is the same regardless of whether you use direct onboarding. Enabling direct onboarding is an opt-in setting at the tenant level.
- There are some limitations with this method, as below:
- Direct onboarding lets you access all features of Defender for Servers Plan 1. Some features in Plan 2 need the Azure Monitor Agent, which only works with Azure Arc on non-Azure machines.
- We can onboard VMs in AWS and GCP using the Defender for Endpoint agent. If you want to connect your AWS or GCP account to Defender for Servers with multi-cloud connectors, it’s best to deploy Azure Arc.
This concludes our blog post on onboarding Microsoft Defender for Endpoint with servers. Please share your thoughts if you have any questions or feedback.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

