Greetings! In this blog post, we will explore the process of integrating the Azure Virtual Network Manager (AVNM) into Azure Landing Zones. This integration is essential for optimizing network management and enhancing the overall architecture of the Azure cloud environment.
Introduction:
AVNM is a comprehensive network management service within Microsoft Azure that simplifies virtual network planning, deployment, and management across large-scale environments. It enables organisations to centrally manage required network topology and secure their infrastructure, offering features like consistent policy enforcement, seamless connectivity, and route management.
Please visit my earlier blog post to learn more about this service and its functions: Azure Virtual Network Manager (AVNM).
AVNM service enables to configure, deploy, and manage the virtual networks with the below configurations:
- Connectivity model/topology configuration.
- Security configuration.
- User-defined route (UDR) management.
- IP address management (IPAM).
Connectivity Configuration:
You can create different network layouts based on your needs to keep the connectivity configuration consistent across your cloud network infrastructure. A connectivity configuration gives you three layout options: mesh, hub-and-spoke, or hub-and-spoke with direct connections between spoke virtual networks.
- Azure Virtual Network Manager can support the traditional Hub-Spoke, mesh, and Hub-and-spoke topology with direct connectivity between spokes. The support for virtual WAN is currently in private preview.
- When you modify your network infrastructure in the Azure cloud, Azure Virtual Network Manager is crucial in preserving the topology you have established and maintaining the existing connectivity configuration of the model deployed.
- For instance, when you create a new Virtual Network (VNET) for the application in a subscription as spoke Vnet, the spoke Vnet must peer with the hub VNet to invoke the required connectivity, such as ExpressRoute or VPN.
- Using the AVNM service, we can automate the newly created spoke VNets peering into Hub Vnet. This automated process simplifies infrastructure management and ensures your network remains organised and efficient, reflecting any updates or changes to the overall architectural design.
- To automate the configuration of spoke vnets, define dynamic spoke VNets with the attribute of tag or subscription id. Dynamic membership allows you to select multiple virtual networks at scale if they meet defined attributes.
- The Dynamic membership will create an Azure Policy with defined conditional attributes and monitor for any changes to spoke VNet. Azure Virtual Network Manager automatically adapts to modifications in your cloud network resources to help maintain optimal connectivity and operational continuity.
- Azure Virtual Network Manager will intelligently manage and implement the necessary adjustments to ensure seamless connectivity with that new spoke and its associated virtual networks.
Deployment for existing landing zone:
- Most customers already have a network topology model, typically using a hub-and-spoke configuration. We can utilize AVNM to import their configuration into AVNM service.
- First, create an AVNM instance in your network or connectivity subscription. Then, choose the hub-and-spoke model and select the existing hub-spoke Virtual Networks (VNETs).
- When you deploy this configuration, the Virtual Network Manager automatically creates the necessary peerings. In contrast, any pre-existing peerings will remain intact. This process ensures that there is no downtime.
- As metioned eariler, you can have a dynamic network group in AVNM to keep your future VNETs added into AVNM with a existing topology.
Security Configuration:
Security admin rules comprise global network security restrictions that implement the security policies defined within a rule collection for virtual networks. These rules facilitate network traffic management by allowing, always allowing, or denying access across virtual networks within specified network groups.
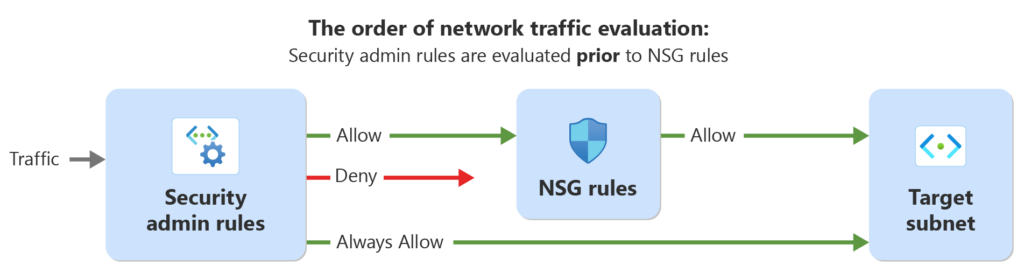
- In security administration, traffic rules can be categorized into three main actions: Allow, Always Allow, and Deny. When these rules are established, they should be assessed first in the evaluation process.
- Following this, network security group rules come into play. These rules are not network security group rules. However, these will be applied on top of Network Security Group (NSG) rules. Security admin rules will be evaluated before NSG rules.
- Always Allow Rule
- Direct traffic to resource
- Termination of further evaluation by NSG rules
- Benefits of enforcing traffic
- Deny Rule
- Stopping traffic from reaching the destination
- Implications of immediate traffic denial
- Allow Rule
- Allows NSG rules to handle the traffic differently if needed.
- NSG rules are evaluated after allow rules.
- It is essential to recognise that security administration rules do not apply to virtual networks and that a virtual network manager does not govern them.
Deployment for existing landing zone:
- We can establish security configurations for your current landing zones, enabling you to permit or restrict specific traffic according to your requirements. In certain scenarios, it is possible to allocate separate Automated Virtual Network Management (AVNM) instances exclusively for security configurations, particularly if a dedicated team is available to manage them.
- Alternatively, if such a team isn’t present, you can implement security admin rules alongside the existing AVNM instance, integrating it with the network topology configuration instance for a more streamlined approach.
- Establishing default security measures across cloud network resources enhances flexibility and control in traffic management. We can also create exceptions to allow application traffic as required.
User-defined route (UDR) management:
AVNM enables us to define and manage routing behaviour using User-Defined Routes (UDRs), streamlining automation and simplifying the process. While you can create UDRs manually or through custom scripts, these methods can lead to errors. With UDR management in the virtual network manager, you gain a centralised hub for effective routing management.
- In the AVNM, you set up routing by configuring and adding rule collections. These rule collections define the User Defined Routes (UDRs) needed for a specific network group.
- The route rules explain how to handle routing for the subnets or virtual networks in that group. After you finish the configuration, you must deploy it for the changes to take effect. All routes are stored in a route table within a managed resource group.
- For example, when you create a new Virtual Network (VNET) for the application in a subscription as a spoke Vnet, the spoke Vnet needs access to the on-premise or internet through a Firewall. The AVNM will automatically apply the UDRs needed when the VNET is added dynamically to the network group in AVNM.
Deployment for existing landing zone:
- We can establish UDR configurations for your current landing zones, enabling consistent route management. In certain scenarios, it is possible to use dedicated Automated Virtual Network Management (AVNM) instances exclusively for route and network topology configurations, particularly if a dedicated team is available to manage them.
- Alternatively, if you need a separate AVNM instance, isolate it with the network topology and the UDR management approach.
- When a route table with existing UDRs is present, Azure Virtual Network Manager will create a new managed route table that includes both the existing routes and new routes based on the deployed routing configuration.
IP address management (IPAM):
Azure Virtual Network Manager offers a comprehensive solution for IP address management (IPAM), allowing for centralised oversight of IP addresses within your virtual networks through IP address pools. Critical features of IPAM in Azure Virtual Network Manager include:
– The ability to create pools for effective IP address planning.
– Automatic assignment of non-overlapping CIDR ranges to Azure resources to streamline management.
– Options to reserve specific IP addresses for targeted needs.
– Mechanisms to prevent overlapping address spaces between on-premises and cloud environments.
– Monitoring capabilities for tracking IP and CIDR usage and allocations within a pool.
– Support for IPv4 and IPv6 address pools, ensuring flexibility for various networking requirements.
These features collectively enhance the management and organization of IP addresses in the Azure environment. The IP address management (IPAM) feature in Azure Virtual Network Manager is now in preview. It is available in the selected regions during preview:
- The Key Components of IPAM
A. Managing IP Address Pools
1. Definition and purpose of IP address pools.
2. Structure and organization of pools.
– Root pool: Definition and significance.
– Child pools: Subset relationship with root pools.
3. Hierarchy and management of pools.
– Up to seven layers of pools for granular control. - B. Allocating IP Addresses to Azure Resources
1. Assigning CIDRs to Azure resources. Examples of resources (e.g., virtual networks).
2. Benefits of allocation for identifying CIDR usage.
3. Static CIDR allocation.
– Use cases for static CIDRs (currently unused or unsupported resources).
4. Efficient management of allocated CIDRs.
– Release process upon resource deletion. - C. Delegating Permissions for IPAM
1. Importance of delegating access to users.
2. Features of delegated permissions.
– Access to pool visibility and selection.
– Viewing usage statistics and associated resources.
3. Detailed usage statistics provided:
– Total number of IPs in the pool.
– Percentage of allocated pool space.
4. Overview of IP usage for better management and planning. - D. Simplifying Resource Creation
1. Automatic CIDR allocation during resource creation.
– Focus on CIDR-supporting resources (e.g., virtual networks).
2. Mechanism to prevent overlap of allocated CIDRs.
– Maintaining network integrity and conflict avoidance.
Conclusion
With Azure Virtual Network Manager, businesses can efficiently manage hybrid networking scenarios, define policies for network segmentation, and gain a unified view of their global network topology. It streamlines the complexity of multi-region and multi-subscription network management, reducing the overhead of maintaining network configurations manually across numerous resources. Using AVNM, organisations can improve operational efficiency, enhance security posture, and ensure optimized performance of their Azure-based network resources.
This service is particularly beneficial for those with complex network architectures or who manage large-scale Azure environments. It enables them to scale and adapt their network infrastructure as business needs evolve.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

