The network topology and connectivity design are essential for building a solid foundation in Azure cloud architecture. A well-structured network facilitates connections within landing zones, enabling seamless interaction with Azure services, external users, and on-premises infrastructure. This connectivity is the backbone that supports all operational capabilities across the network.
In this blog, let’s work out the best practices for Azure networking services to build the foundations for Azure Cloud.
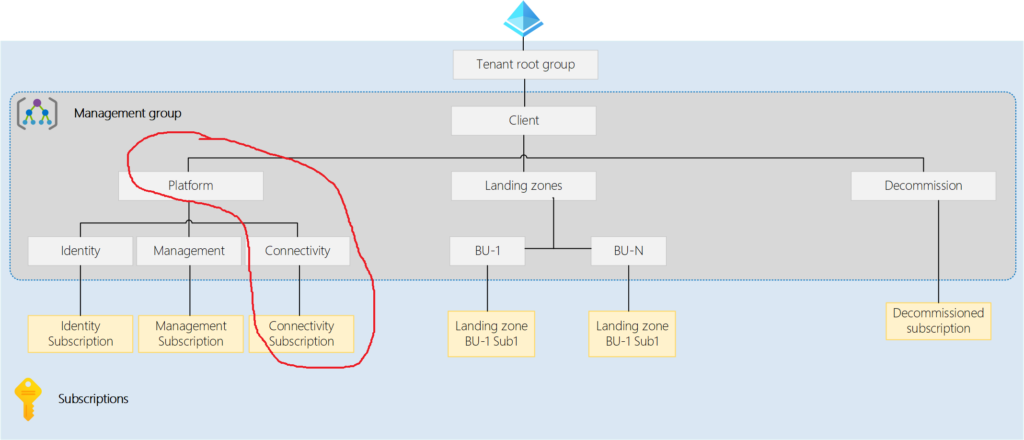
1. Connectivity Management Group:
A dedicated management group for hosting the networking subscription, which facilitates the hosting of networking services, is mandatory. These subscriptions facilitate hosting essential Azure networking resources required for the platform, including Azure Virtual WAN, Virtual Network Gateways, Azure Virtual Network Manager, Azure Firewall, and Azure DNS private zones.
Design Recommendations: Microsoft recommends a dedicated management group and specific subscriptions dedicated to connectivity, typically representing a singular subscription for most organisations.
2. Network Topology:
Network topology plays a crucial role in the architecture framework of a Landing Zone. It outlines the communication pathways for applications across organisational boundaries, whether in the cloud or on-premises. The Azure landing zones conceptual architecture recommends one of two networking topologies:
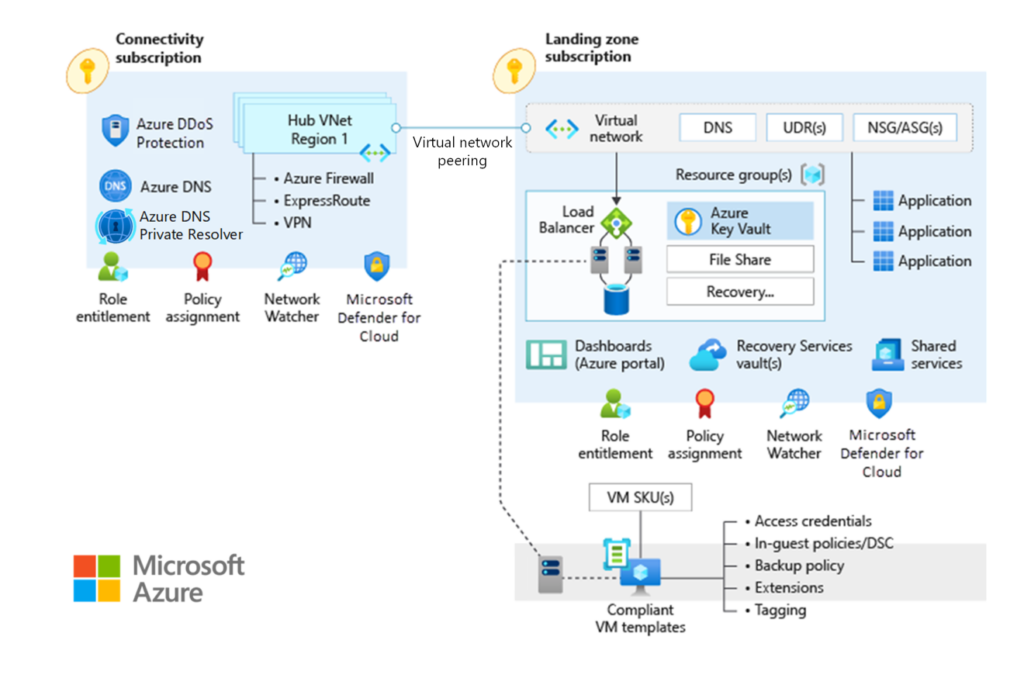
2.1 Hub-and-Spoke Network Topology:
- It is suitable for organisations that plan to deploy resources within a single region and do not require a full mesh network.
- This topology is ideal for scenarios with fewer remote connections per region and provides complete control and granularity for manual configuration.
- This option involves manually configuring the Azure network routing policy as needed.
The diagram below shows all the relevant services that provide network and connectivity with Hub and Spoke topology (Source: Microsoft):
2.2 Virtual WAN:
- This pattern is designed to address large-scale interconnectivity needs and is managed by Microsoft, simplifying complexity.
- This is a software-defined WAN (SD-WAN) deployment that integrates a large-scale branch network, including VPN connections, directly into Azure.
- This is best suited for organisations establishing deployments across various regions and enabling global connectivity.
- Microsoft recommends using Azure vWAN architecture for this option in the landing zone.
The diagram below shows all the relevant services that provide network and connectivity with virtual WAN topology (Source: Microsoft):
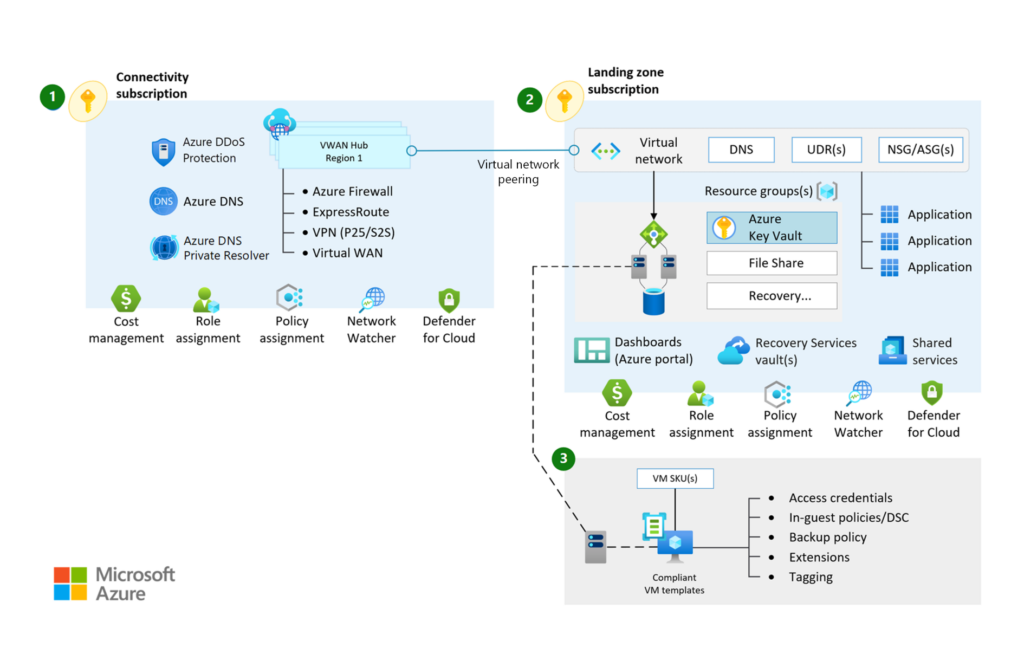
Design Recommendations: Microsoft recommends using Virtual WAN for organisations needing hub-and-spoke architectures across multiple Azure regions with global transit connectivity and reduced network management.
3. Azure Virtual Network Manager (AVNM)
This is an excellent addition to the Azure Cloud’s networking services. The AVNM service offers centralised management and governance for networking within Azure landing zones. It includes four key features: networking topology, security admin rules, route management, and IP address management.
3.1Networking topology
AVNM’s network topology feature automates virtual network peering. This makes it easier to manage large and complex network setups at scale, like mesh or hub-and-spoke.
3.2 Security Admin Rules
The security admin rules feature lets you specifically allow or deny specific network traffic, even if the network security groups (NSGs) at the subnet or network interface levels say otherwise. Application teams can’t change these rules.
3.3 Route Management
With UDR management in the virtual network manager, you have a central place to handle and maintain routing behaviour.
3.4 IP Address Management
IP address management (IPAM) helps you to manage IP addresses in your virtual networks using pools of IP addresses.
The diagram below shows how the AVNM centrally manages the virtual network in the landing zone.
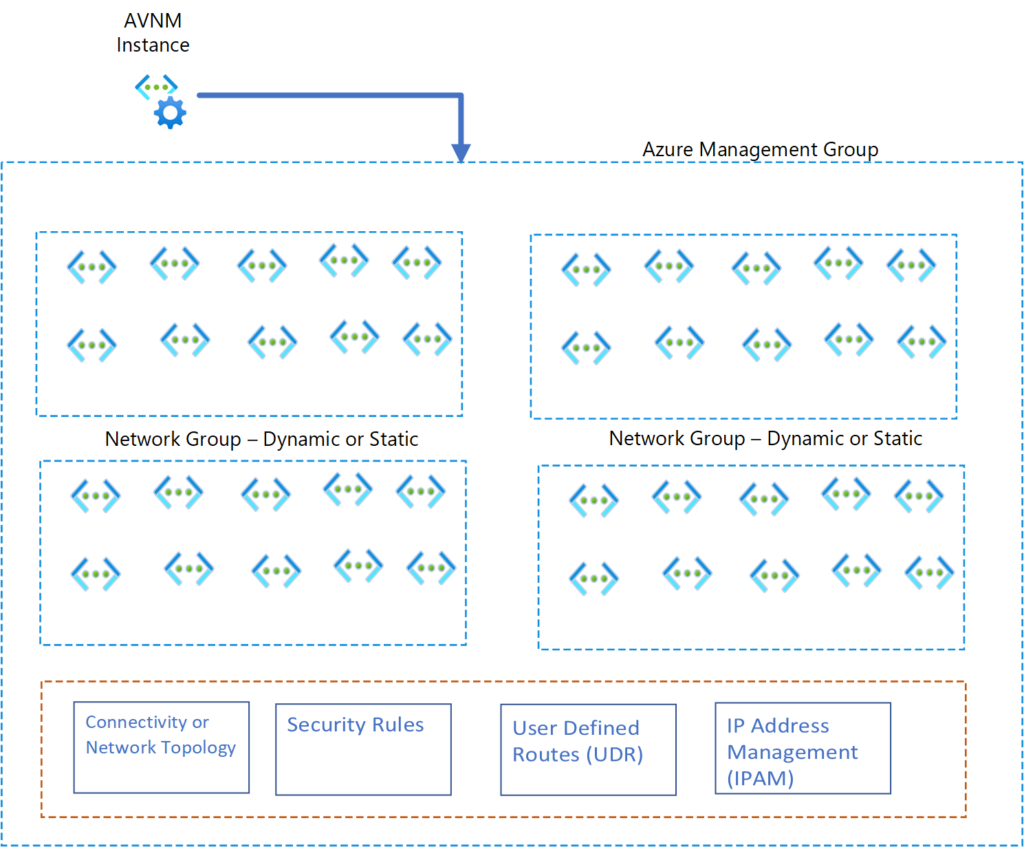
Design Recommendations: Use AVNM service to automate and centrally control the network topology, security admin rules, route management and IPAM. As a best practise, the AVNM instance should be established within the connectivity subscription to manage virtual networks effectively, explicitly focusing on the appropriate Azure management group.
4. Connectivity to Azure
When establishing connectivity to the Azure platform, it is crucial to consider various connectivity patterns that align with the organisation’s specific requirements. This thoughtful approach ensures the right connectivity strategies are in place and helps maintain and control your network security boundaries effectively.
Connectivity to Azure is pivotal in bridging your on-premises infrastructure with the Azure cloud, enabling seamless integration and expansion of your network capabilities. Organisations can leverage two primary connectivity methods, each with unique advantages, that can be used independently or in combination, depending on the specific use case and operational needs.
4.1 ExpressRoute:
- ExpressRoute provides a private connection between your on-premises networks and Azure, bypassing the public internet.
- ExpressRoute offers higher reliability, faster speeds, and lower latencies than standard internet connections.
- It is ideal for organizations requiring consistent performance, security, and compliance for sensitive data transfer.
- This service has different SKUs and models that fit the requirements.
4.2 Azure VPN:
- VPN service employs an encrypted connection over the public internet, making it suitable for secure communications without requiring dedicated lines.
- Azure VPN gateways can connect your on-premises networks securely to Azure, providing flexibility for mobile users and remote locations while maintaining a cost-effective solution.
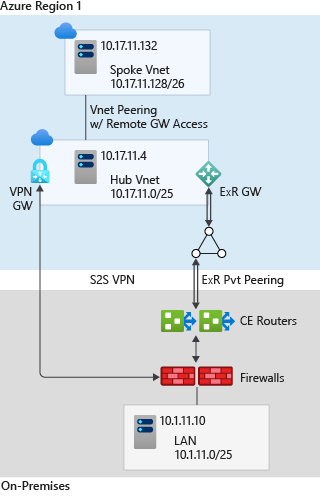
Design Recommendations: Use ExpressRoute for primary connectivity from an on-premises network to Azure, with VPNs as a backup for enhanced resiliency.
5. Network Security
Azure provides a range of integrated network security features and allows the use of non-Azure virtual network appliances.
5.1 Plan for Application Delivery
Key Azure services that can enhance your connectivity and security include application delivery:
- Azure Load Balancer: This service ensures high availability for applications at the regional level by effectively distributing incoming traffic.
- Azure Application Gateway: This service facilitates the secure delivery of HTTP/S applications within a specific region, optimizing performance and security.
- Azure Front Door: This offers a secure solution for delivering HTTP/S applications across multiple Azure regions, enhancing global accessibility.
- Azure Traffic Manager: This enables the efficient delivery of applications globally, optimizing performance and availability for users worldwide.
Design Recommendations: When assessing application delivery connectivity services, consider all workload requirements and select the appropriate service from above. Use the Azure DDoS Protection plan for public endpoints in your virtual networks. Implement a Web Application Firewall (WAF) in landing zones to protect inbound HTTPS traffic from the Internet.
5.2 Inbound and Outbound Connectivity
These services provide essential tools for managing secure internet connectivity in a cloud environment. The strategy for managing inbound and outbound internet connectivity is to ensure secure access for public use. Notably, starting at the end of September 2025, Azure will discontinue default outbound internet access for virtual machines (VMs).
- Azure Firewall or Network Virtual Appliances (NVA)
- Azure Web Application Firewall
- Azure Application Gateway
- Azure Front Door
- NAT Gateway
Design Recommendations: For enhanced security, utilize Azure Firewall or NVA to manage ingress and egress traffic. Use a NAT gateway for the landing zones not connected to the hub virtual network for internet connectivity.
5.3 Connectivity to PaaS
5.3.Accessing Azure Platform as a Service (PaaS) is crucial, as these services are typically available through publicly accessible endpoints on the Microsoft backbone network. However, companies with specific security requirements may need to limit access to these public endpoints. To address this need, Azure offers several optional features designed to enhance security or provide complete privacy.
There are several strategies for managing public service access, including:
- Access Restrictions via System-Managed Identities: This method allows for controlled authentication and authorization using managed identities linked to Azure resources.
- Trusted Azure Services: Certain Azure services can be configured to communicate securely with each other without requiring public access.
- Virtual Network Injection: This technique connects Azure services directly to a virtual network, enhancing security.
- Azure Private Link: This feature enables private connectivity to PaaS services, ensuring traffic does not traverse the public internet.
- Virtual Network Service Endpoints: Service endpoints extend your virtual network’s private address space for specific Azure services, enabling secure and direct connectivity.
Design Recommendations: Access to Azure PaaS services should be enabled with either Azure Private Link or virtual network injection to limit public access to Azure services, which is essential for maintaining security.
5.4 DNS Resolution
DNS is a key element in landing zone architecture. Some organisations may prefer to use their current DNS investments, while others might update their infrastructure to leverage native Azure capabilities during cloud adoption.
Design Recommendations: Use Azure Private DNS zones for environments needing only Azure name resolution. For name resolution across Azure and on-premises, use DNS Private Resolver with Azure Private DNS zones, or use existing DNS infrastructure like Windows Server Active Directory-integrated DNS, deploy it on at least two virtual machines and configure virtual network settings to use these custom DNS servers.
By understanding the different Azure networking service and their implications, organisations can make informed decisions about their connectivity strategies in Azure, ensuring that network security, performance, and scalability are effectively addressed.
To learn more about the services mentioned in this article, I recommended reading the blog post using the below links:
- https://skylinetechnology.org/azure/how-can-resilience-be-improved-with-express-route-in-azure-connectivity-part-2/
- https://skylinetechnology.org/azure/using-azure-ipam-for-landing-zones-concepts-and-reasons/
- https://skylinetechnology.org/azure/how-to-integrate-azure-private-endpoint-with-dns-for-the-best-practice/
- https://skylinetechnology.org/azure/innovative-uses-of-azure-virtual-network-manager-in-landing-zones-environments/
- https://skylinetechnology.org/azure/analysis-of-azure-private-endpoint-service-endpoint-and-private-links/
- https://skylinetechnology.org/azure/azure-network-security-group-a-look-back-and-a-look-forward/
- https://skylinetechnology.org/azure/evolve-cloud-security-as-zero-trust-model-with-azure-networking-services/
- https://skylinetechnology.org/azure/how-can-resilience-be-improved-with-express-route-in-azure-connectivity-part-2/
- https://skylinetechnology.org/azure/azure-networking/how-can-resilience-be-improved-with-express-route-in-azure-connectivity-part-1/

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

