The adoption of containerised applications has surged due to their flexibility, scalability, and efficiency. However, this growth also brings new security challenges. Containers often operate in shared environments, increasing the risk of vulnerabilities and potential threats from both internal and external sources. With the adoption of Zero Trust, we need to detect and prevent unauthorised access and attacks on containers.
Microsoft Defender for Container service is essential for securing these containerised environments. It offers comprehensive visibility, threat detection, and automated responses to security incidents. Let’s deep dive into Defender for Containers workloads in the blog post.
Microsoft Defender for Cloud – Container Protection
Microsoft Defender for Containers is a cloud-native solution that enhances and monitors the security of containerised assets, including Kubernetes clusters, nodes, workloads, and images, across multicloud and on-premises environments.
To give you some more understanding of this service plan. Previously, Microsoft Defender for Kubernetes and Microsoft Defender for Container Registries were two separate services. In early 2022, Azure introduced a new service plan: Defender for Containers. The new plan combines the capabilities of the two existing Microsoft Defender for Cloud plans, introducing additional features.
Defender for container focuses on four key areas:
1. Security Posture Management: Continuously monitors Kubernetes APIs and container workloads to assess risks, detect misconfigurations, and support enhanced risk hunting.
2. Vulnerability Assessment: Performs agentless vulnerability scans of container images and running containers, offering remediation guidance and exploitability insights.
3. Run-time Threat Protection: Provides advanced threat detection for Kubernetes environments, aligned with the MITRE ATT&CK framework, enabling efficient threat investigation and response.
4. Deployment & Monitoring: Monitors Kubernetes clusters for missing sensors and ensures seamless deployment of sensor-based capabilities across standard monitoring tools.
To learn more about the support matrices, visit the Microsoft page.
How does Defender for Containers work?
The solution supports Kubernetes workloads in both Azure and non-Azure environments. It enables easy deployment and maintenance on the Kubernetes control plane, providing customers with enhanced visibility and management of their workloads. Users can utilise Kubernetes-native tools for streamlined operations and consistent management across all environments.
The solution offers tight integration with Azure Kubernetes Service (AKS), providing a comprehensive security profile that enables robust security management within Azure-hosted Kubernetes clusters. Furthermore, it extends its functionality to Azure Arc-connected clusters, serving as a cluster extension that effectively manages multi-cloud and on-premises scenarios. This integration enables users to maintain governance and security compliance across diverse infrastructures, thereby maximising both efficiency and control in a hybrid cloud environment.
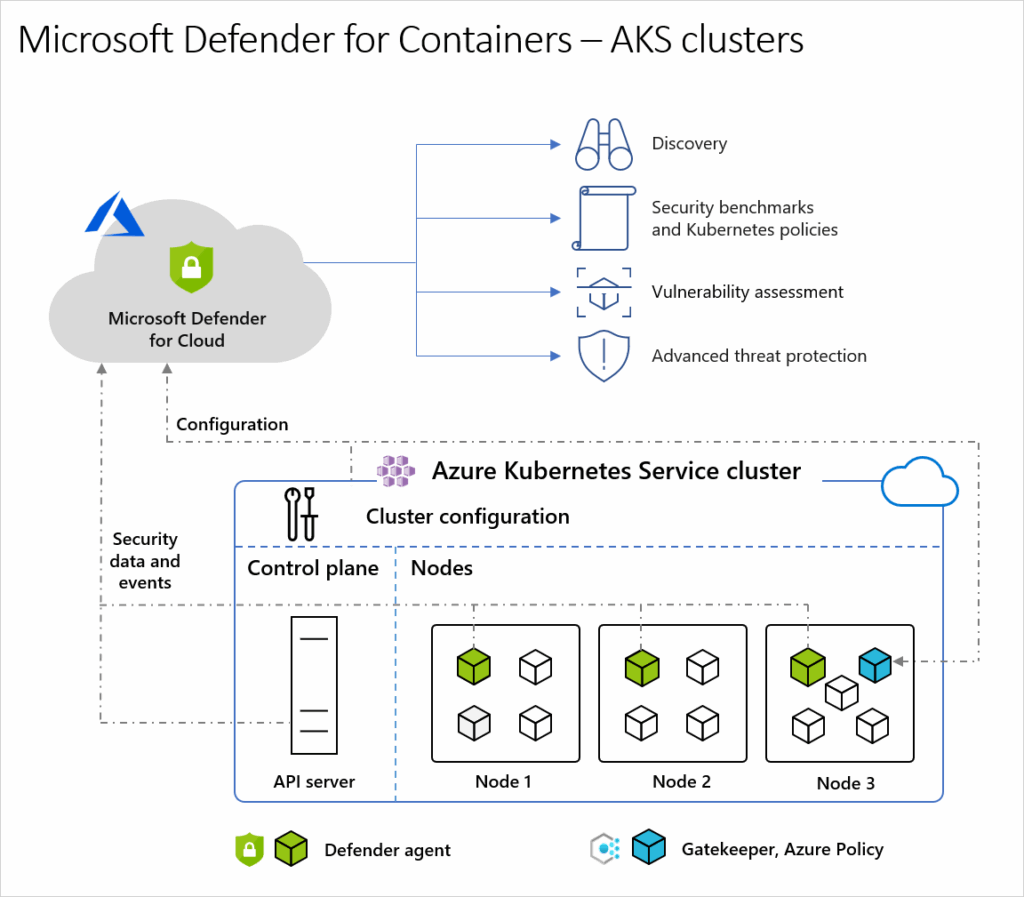
When Defender for Cloud protects a cluster in Azure Kubernetes Service, audit log data is collected automatically and agentlessly at no extra cost. Key components for complete protection include:
- Defender Sensor: A DaemonSet on each node that collects host signals using eBPF technology for runtime protection. It functions as a data pipeline registered with a Log Analytics workspace, although audit logs are not stored there. The sensor is deployed as an AKS Security profile.
- Azure Policy for Kubernetes: A pod that extends open-source Gatekeeper v3, registered as a webhook to enforce policies across clusters consistently. It’s deployed as an AKS add-on on one node in the cluster.
Multi-Cloud and Hybrid Support
Defender is built with flexibility for multi-cloud and on-premise Kubernetes clusters. The following options are supported:
- Support for AWS (EKS), GCP (GKE), and On-Premises Kubernetes: Defender extends its protections beyond Azure, providing a unified security approach for diverse environments.
Core Capabilities of Defender for Containers
The below section will delve into the intricate functionality of the container defender, offering a comprehensive overview of its operational mechanisms and the insightful results produced by each of its distinctive features.
Security Posture Management
Let’s discuss the features under the security posture management for the container workloads:
- Agentless Discovery for Kubernetes: Offers API-based discovery of Kubernetes clusters, configurations, and deployments without a footprint.
- Agentless Vulnerability Assessment: Evaluates cluster nodes and container images for vulnerabilities, providing registry/runtime recommendations, quick scans, daily updates, and exploitability insights, which enhance the security graph for risk assessment and threat hunting.
- Comprehensive Inventory capabilities: Enables the exploration of resources, pods, services, repositories, images, and configurations through the security explorer for effective asset management.
- Enhanced Risk-Hunting: Enables security administrators to identify posture issues in containerised assets using built-in and custom queries, alongside security insights.
- Control Plane Hardening: Continuously checks cluster configurations against applied initiatives, generating security recommendations for misconfigurations available on Defender for Cloud’s Recommendations page to aid in remediation.
- Binary Drift Detection – Defender for Containers offers a sensor-based feature that alerts you to security threats by identifying unauthorised processes in containers. You can set drift policies to define alert conditions, helping differentiate between legitimate actions and threats. For more details, see Binary Drift Protection (preview).
- Kubernetes Data Plane Hardening – To safeguard Kubernetes workloads, install the Azure Policy for Kubernetes, which provides best practice recommendations. Kubernetes cluster policies monitor API requests against best practices before they are saved.
- Attack Path Analysis: A graph-based algorithm that scans the cloud security graph. The scans expose exploitable paths that attackers might use to breach the Kubernetes environment.
Vulnerability Management
Defender for Containers scans cluster node OS, application software, and container images in various registries (ACR, ECR, GAR, GCR, and others) for agentless vulnerability assessment. In public preview for AKS, it also conducts daily scans of running containers for updated assessments, regardless of the image registry. Microsoft Defender Vulnerability Management data is incorporated into the Cloud Security Graph for risk and attack path analysis.
Defender for Containers pulls images from the registry and runs them in an isolated sandbox using Microsoft Defender Vulnerability Management for Azure environments. The scanner generates a list of known vulnerabilities. Vulnerabilities are ranked by severity with actionable remediation guidance, making it easier for dev teams to prioritise fixes.
The list of vulnerability assessment features is:
| Feature | Description |
| Container registry vulnerability assessment | Vulnerability assessment for images in container registries. The supported registries are: ACR, ECR, GAR, GCR, Docker Hub, JFrog Artifactor |
| Runtime container vulnerability assessment | Registry agnostic vulnerability assessment of container running images |
| Vulnerability assessment of containers running images from supported registries | Vulnerability assessmentof containers running images from supported registries |
| Registries and images | Supported * Container images in Docker V2 format * Images with the Open Container Initiative (OCI) image format specification. Unsupported * Super-minimalist images, such as Docker scratch images, are currently unsupported * Public repositories * Manifest lists |
Run-time protection for Kubernetes nodes and clusters
Microsoft Defender for Containers provides real-time threat protection for supported containerised environments, generating alerts for any suspicious activity detected. This functionality enables users to promptly address security issues and enhance the overall security posture of their containers.
The threat protection services extend to Kubernetes environments at various levels, including the cluster, node, and workload. It utilises both sensor-based coverage, which requires the deployment of the Defender sensor, and agentless coverage, which analyses Kubernetes audit logs to identify potential threats. Security alerts are triggered only for actions and deployments that happen after Defender for Containers has been enabled in your subscription.
Additionally, Microsoft Defender for Containers introduces host-level threat detection, featuring over 60 new Kubernetes-aware analytics, AI capabilities, and anomaly detection methods based on runtime workloads. The list of runtime protection features is:
| Features | Description |
| Control plane detection | Detection of suspicious activity for Kubernetes based on the Kubernetes audit trail. |
| Workload detection | Monitors containerised workloads for threats and gives alerts on suspicious activities. |
| Binary drift detection | Detects a binary of runtime container from a container image. |
| DNS Detection | DNS Detection capabilities, which are currently in preview. |
| Malware detection | Detection of malware on AKS Nodes |
| Response actions in XDR | Provides automated and manual remediation in Microsoft XDR. This is currently in preview. |
| Advanced hunting in XDR | View cluster incidents and alerts in Microsoft XDR. This is currently in preview. |
Deployment & Monitoring
Microsoft Defender for Cloud offers a comprehensive overview of the security posture for hybrid cloud workloads through its interactive Overview dashboard. It also delivers a unified perspective on threat detection and protection for secured resources via the interactive Workload Protections dashboard.
The Defender for containers provides benchmarking against CIS benchmarks for Kubernetes clusters. Enforce security standards and governance with Azure policies that ensure compliance across the Kubernetes environments. We can configure these policies to enforce and mandate best practices for future workloads. Protect the Kubernetes containers’ workloads with best practice recommendations.
Enable the Defender for Containers plan
When you enable the Microsoft Defender for Containers plan via the Azure portal, it automatically configures all necessary capabilities and installs the required components to deliver the plan’s protections. This process also involves assigning a default workspace.
However, if you would like to assign a custom workspace instead, you have the option to do so using Azure Policy.
To activate Defender for Containers on your subscription, follow these steps:
- Sign in to the Azure portal.
- Use the search bar to find and select “Microsoft Defender for Cloud.”
- In the Defender for Cloud menu, click on “Environment settings.”
- Choose the appropriate Azure subscription from the list.
- On the Defender plans page, locate the Containers plan and toggle it to the “On” position.
- Finally, click “Save” to apply your changes.
By following these steps, you can ensure that Defender for Containers is successfully enabled for your subscription.
- You can use the Azure Policy
Configure Microsoft Defender for Containers to be enabled, to enable Defender for Containers at scale. - To onboard multiple subscriptions at once, you can use this script.
The Defender for Containers plan can be enabled, and all relevant components can be deployed through various methods. This guide outlines the steps to achieve this using the Azure portal. It details how to deploy the Defender sensor using REST API, Azure CLI, or a Resource Manager template.
To deploy the Defender sensor in Azure, follow these steps:
- Sign in to the Azure portal.
- Search for and select Microsoft Defender for Cloud.
- Navigate to the Recommendations page.
- Locate and select the recommendation for enabling the Defender profile on Azure Kubernetes Service clusters.
- Select all affected resources.
- Click “Fix” to implement the changes.
Benefits and Differentiators
In this section, we will discuss the benefits of Defender for Containers and how it distinguishes itself from other tools on the market.
Multi-Cloud and Hybrid Support
Microsoft understands that modern infrastructure spans both cloud and on-premises environments. Defender supports: Amazon EKS and Google GKE, On-premises Kubernetes clusters and Custom container registries. This flexibility enables you to maintain a consistent security posture regardless of where your containers run.
Developer and DevSecOps Integration
Defender integrates seamlessly into DevOps pipelines and is Secure by design: Native support for GitHub and Azure DevOps, Policy enforcement within CI/CD workflows and Visibility without slowing innovation.
Unified Security Across the Container Lifecycle
From image creation to runtime monitoring, Defender for Containers offers continuous protection at every stage: Pre-deployment, Deployment and Runtime.
Conclusion
As containers become the foundation of modern application development, securing them effectively is no longer optional—it’s critical. Microsoft Defender for Containers combines powerful vulnerability scanning, real-time threat detection, policy enforcement, and DevOps integration to deliver comprehensive, scalable container security.
Whether you’re running workloads in Azure, across multiple clouds, or in hybrid environments, Defender equips you with the tools and visibility needed to stay ahead of threats, without slowing down your development velocity.
This blog post covers container security architecture in Microsoft Defender for Cloud. It offers valuable insights for both experienced professionals and newcomers looking to secure containerised environments.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

