Another end of month, I`m here to provide a single post for Azure updates on previous month. This blog, we will be covering up august month updates from Azure. Each update on this blog is not an exhaustive list of all the monthly updates. I would like to call out most specific updates from Infrastructure technologies (compute, storage, networking, identity, monitoring & security, etc..) and have categorised the updates based on high level sections.
Azure Compute
Selective disks backup for Azure Virtual Machine
Azure Backup supports backing up all disks (OS and Data disks) in a VM using backup solution for Azure VMs. From August 2020, Microsoft announced the public preview of selective disks backup and restore capability for Azure Virtual Machines. Using the selective disks backup functionality, you get an option to backup a subset of the data disks in a VM. This provides an efficient and cost-effective solution for your backup and restore needs. Each recovery point contains only the disks that are included in the backup operation which further allows you to have a subset of disks restored from the given recovery point during the restore operation. This applies to both restore from snapshot and vault.The benefits are cost and quicker backup & restore operation.
Improvements to Azure VM backups are now available
Azure Backup now has even greater support and functionality for Azure VM backups. Azure Backup is introducing restoring Unmanaged VMs/Disks as Managed VMs/Disks to provide the benefit of Managed disks for customers who are currently backing up their unmanaged disks. This feature isn’t available for unmanaged encrypted VMs.
Azure Backup now supports Replace existing disks as an option for VMs that have Managed Service Identities (MSI) Both User assigned Identities and System assigned Identities.
Azure Backup now supports backup & restore of Virtual Machine Scale Sets in the orchestration mode.
Encryption of backup data using customer managed keys is in public preview
When backing up Azure Virtual Machines, we can now encrypt your data using keys owned and managed by customer. Azure Backup lets you use your RSA keys stored in the Azure Key Vault for encrypting your backups. The encryption key used for encrypting backups may be different from the one used for the source. The data is protected using an AES 256 based data encryption key (DEK), which is, in turn, protected using your keys stored in the Key Vault. This gives you full control over the data and the keys.
The scenario works with below pre-requisite:
- This feature allows you to encrypt new Recovery Services vaults only. Any vaults containing existing items registered or attempted to be registered to it aren’t supported.
- Once enabled for a Recovery Services vault, encryption using customer-managed keys can’t be reverted back to using platform-managed keys (default). You can change the encryption keys according to your requirements.
- The Recovery Services vault can be encrypted only with keys stored in an Azure Key Vault, located in the same region. Also, keys must be RSA 2048 keys only and should be in enabled state.
Azure Database
Data encryption with customer managed keys for Azure MySQL & PostgreSQL-single server Postgres database
Data encryption with customer-managed keys for Azure Database for MySQL & PostgreSQL enables you to bring your own key (BYOK) for data protection at rest. It also allows organizations to implement separation of duties in the management of keys and data. With customer-managed encryption, you are responsible for, and in a full control of, a key’s lifecycle, key usage permissions, and auditing of operations on keys.
Data encryption with customer-managed keys for Azure Database for MySQL & PostgreSQL, is set at the server-level. For a given server, a customer-managed key, called the key encryption key (KEK), is used to encrypt the data encryption key (DEK) used by the service. The KEK is an asymmetric key stored in a customer-owned and customer-managed Azure Key Vault instance.
This feature is available in all Azure regions where Azure Database for MySQL & PostgreSQL supports “General Purpose” and “Memory Optimized” pricing tiers.
Configurable backup storage redundancy option for Azure SQL Managed Instance
This feature is in public preview, locally redundant (LRS) and zone redundant (ZRS) storage options have been added to backup storage redundancy, providing more flexibility and choice. With this option we have more cost-effective options for ensuring data is protected in case of planned and unplanned events. Easily configure backup storage redundancy in Azure portal.
The features main capabilities are:
- Redundancy can be configured only during managed instance creation using REST API, ARM template or Azure Portal and cannot be changed later
- Available redundancy options are LRS & ZRS
- When configured redundancy is applied for both PITR and LTR backups
- Redundancy is applied at instance level and cannot be configured per individual managed database.
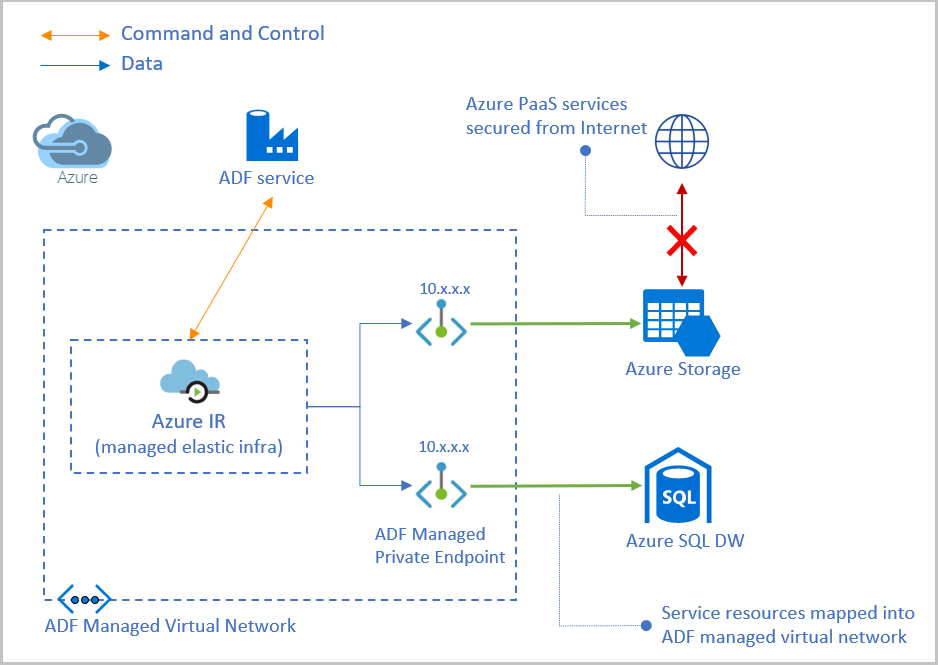
Data Factory managed virtual network support
To enable a more secure and manageable data integration solution, Data Factory now supports managed virtual networks and it’s in public preview. With this feature, we can provision the Azure Integration Runtime in Managed Virtual Network and leverage Private Endpoints to securely connect to supported data stores. The data traffic between Azure Data Factory Managed Virtual Network and data stores goes through Azure Private Link which provides secured connectivity and eliminates data exposure to the internet.
The Managed Virtual Network is associated with Azure Data Factory instance and managed by Azure Data Factory. When you provision Azure Integration Runtime, you can choose to have the Azure Integration Runtime within Managed Virtual Network. Creating an Azure Integration Runtime within managed Virtual Network ensures that data integration process is completely isolated and secure.
Azure Storage
Configure backup for Azure file shares directly from the file share blade
Azure Backup has simplified the experience of configuring backup for Azure file shares by giving the ability to seamlessly enable backup from the file share management blade. With the integration of Azure Backup into file share management blade, we can perform the backup and restore related operations directly from the file share blade, as well as the recovery services vault blade.
Azure Networking & Security
Azure Security Centre—News and updates
There few lists of updates announced for Azure security centre from last month and below is the high-level list:
- A new recommendation has been added to recommend that Security Center customers using management certificates to manage their subscriptions switch to service principals.
- Security Center inspects your VMs to detect whether they’re running a vulnerability assessment solution. If no vulnerability assessment solution is found, Security Center provides a recommendation to simplify the deployment.
- Security Center’s asset inventory (currently in preview) provides a way to view the security posture of the resources you’ve connected to Security Center. Security Center periodically analyzes the security state of your Azure resources to identify potential security vulnerabilities.
Release of new Azure CDN (Microsoft Standard) capability
Customers can now use multiple origins with the same CDN endpoint, using the Azure Portal and Azure CDN APIs to provide a simple, fault tolerant method of load balancing between origins.
With Azure CDN, customers can establish global redundancy and eliminate downtime by designating multiple origins within an Azure CDN endpoint. The redundancy provided by multi-origin spreads risk by probing health of each origin and failing over if necessary.
With the support of multi-origin, customers can route to multiple origins based on path and geo location. For example ,if you want to send all requests originating from the United States to an origin in the United States and all requests originating in Asia to a origin in Asia but fail to the other in case of a downtime. This will help in latency sensitive use cases where customers want minimum latency even during cache misses but at the same time not compromise on availability.
Other Azure Services
Azure Monitor for containers with Azure Portal now supports Kubernetes resource view
Azure portal now includes a Kubernetes resource view, currently in public preview, for easy access to the Kubernetes resources in your Azure Kubernetes Service (AKS) cluster. This option provides a way to improve the developer experience and simplifies dev/test scenarios. This feature is not currently supported in private AKS cluster.
The resource viewer currently includes multiple resource types, such as deployments, pods, and replica sets. To view Kubernetes resources in the Azure portal, any AKS cluster is supported, but if using Azure Active Directory (Azure AD) integration, your cluster must use AKS-managed Azure AD integration. If your cluster uses legacy Azure AD, you can upgrade your cluster
This service supports the following key capabilities:
- See workloads running on your cluster, including the ability to filter resources by namespace
- Find the node an application is running on and their Pod IP address
- See pods in the replica set, ready status of each pod, and images associated with each
- Drill down to individual deployments to see live status and specification details
- Execute on the fly changes to YAML to validate dev/test scenarios
- With Azure Monitor for containers enabled, users can view deployment hierarchy, insights such as CPU usage and memory usage in the Kubernetes resources view, and seamlessly transition to Azure monitor for more in-depth insights
Log Analytics new System Center configuration blade
To maintain existing investment in System Center Operations Manager and use extended capabilities with Azure Monitor, we can integrate Operations Manager with Azure Log Analytics workspace. This allows to leverage the opportunities of logs in Azure Monitor while continuing to use Operations Manager to:
- Monitor the health of IT services with Operations Manager
- Maintain integration with ITSM solutions supporting incident and problem management
- Manage the lifecycle of agents deployed to on-premises and public cloud IaaS virtual machines that you monitor with Operations Manager
Integrating with System Center Operations Manager adds value to your service operations strategy by using the speed and efficiency of Azure Monitor in collecting, storing, and analyzing log data from Operations Manager. Azure Monitor log queries help correlate and work towards identifying the faults of problems and surfacing recurrences in support of your existing problem management process. The flexibility of the query engine to examine performance, event and alert data, with rich dashboards and reporting capabilities to expose this data in meaningful ways, demonstrates the strength Azure Monitor brings in complimenting Operations Manager.
To access the new system center configuration blade, go to you Log Analytics Workspace and select “System Center” from the left-hand navigation bar, under the “Workspace and data sources” group. The new system center blade allows visibility and management of SCOM instances connected to your workspace.
Support to assess physical, AWS, GCP servers now generally available
Azure migrate support to assess physical servers. This feature can also be used to assess virtual machines on Amazon Web Services (AWS), Google Cloud Platform (GCP) or any cloud, on-premise machines of any virtualization or VMware / Hyper-V machines where there is no access to the hypervisor. The assessments offer Azure suitability analysis, migration cost planning and performance-based rightsizing. Support for application dependency analysis (agent-based) is also available. Upto 1000 servers can be discovered per appliance, and any number of servers per Azure Migrate project.
Thanks for your time and hope you had some quick preview of list Azure updates from August month.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

