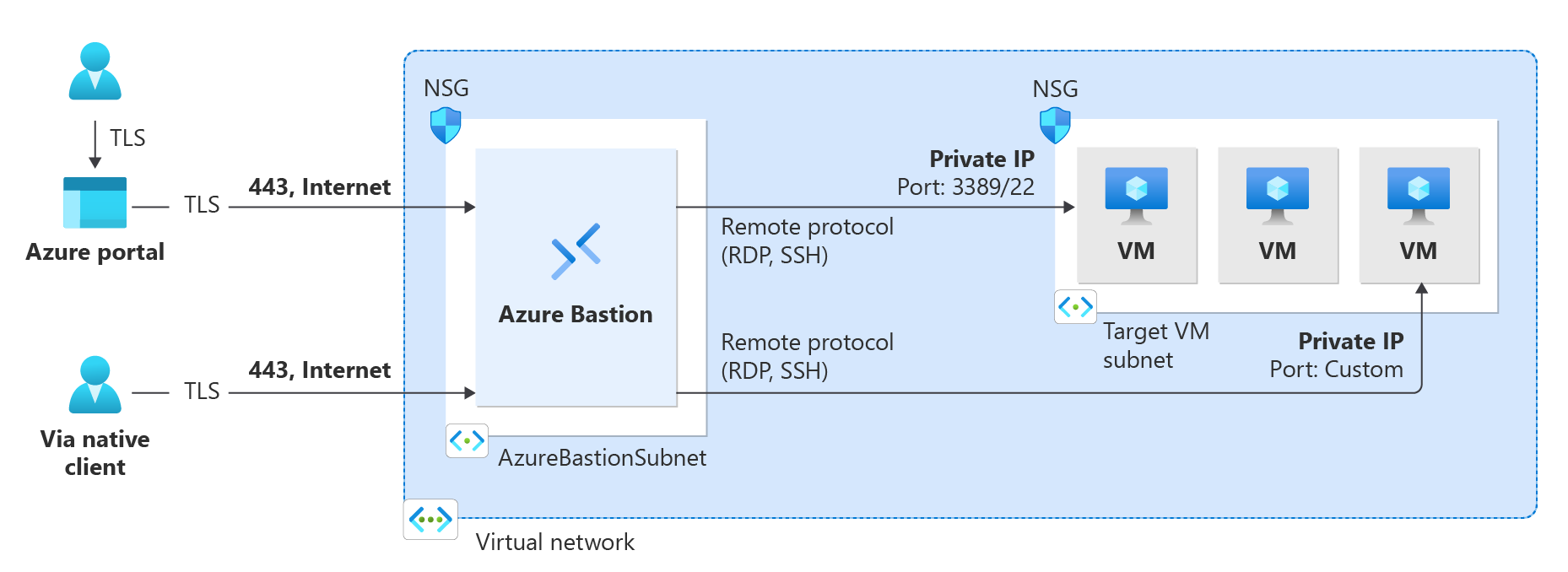
RDP or SSH sessions are commonly used to access target servers as an IT admin. If a jumpbox is unavailable, it is often provided for connecting to the required target server for an RDP/SSH session. In the case of the public cloud, a jumpbox server is placed in the management Virtual Network, which in some environments, may be exposed to the internet with a public IP address. However, from a security standpoint, this is not the most secure way to connect. To address this issue, Azure offers an “Azure Bastion” service that provides fast and seamless RDP and SSH access to virtual machines in the Azure virtual network. The access is enabled via the Azure bastion VM and is not exposed to the public internet. This provides a secure way to access VMs through SSL from the Azure portal without disclosing public IP addresses to connect to.
Azure Bastion is an exceptional service that simplifies the management of access to virtual machines or machine scale sets. It ensures secure access from virtual networks or public domains without needing the resources’ public addresses. With Azure Bastion, users can effortlessly connect to the virtual machine from the Azure portal without requiring additional software or agents. This deployable service allows you to connect to a virtual machine using your browser and the Azure portal or the native SSH or RDP client installed on your local computer. Furthermore, the Azure Bastion service is a fully platform-managed PaaS service you can quickly provision inside your virtual network.
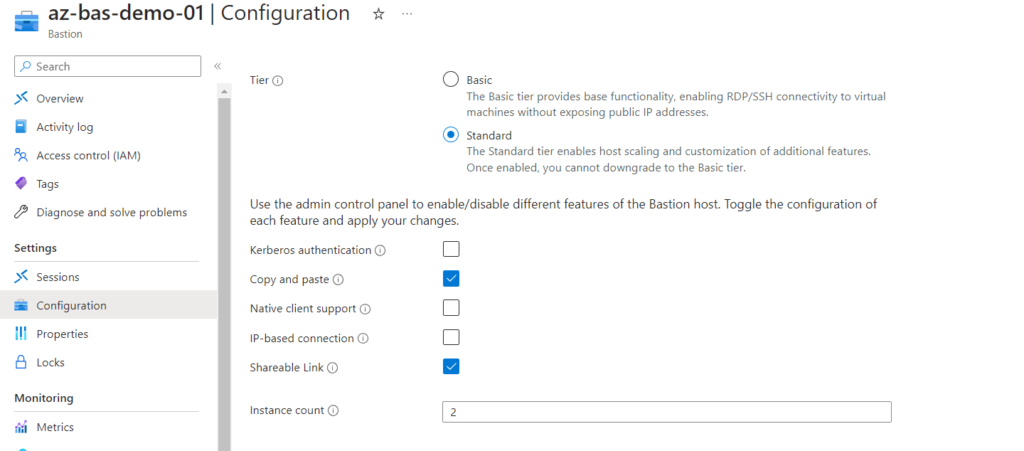
Azure Bastion has two available SKUs, Basic and Standard. Standard SKU has more advanced features like shareable links, host scaling, and more. Azure Bastion requires /26 subnets as the minimum.
With the Bastion Shareable Link feature, you can connect to a virtual machine or machine scale set using Azure Bastion without accessing the Azure portal. When someone who does not have Azure credentials clicks on the shareable link, a web page will open, prompting them to sign in to the target resource via RDP or SSH. The user must provide a username and password or private key, depending on what has been configured for the target resource. The steps to enable shareable links on Bastion:
- The Bastion must be at standard SKU to enable the shareable link features.
2. log in to the Azure portal and select Bastion. Click on configuration.
3. To activate the Shareable Link, choose it from the feature list and click “apply.” You can upgrade to the Standard tier to enable this feature if your SKU is basic.
4. Click on Bastion and select the Shareable link feature. Click + Add to open the Create shareable link page.
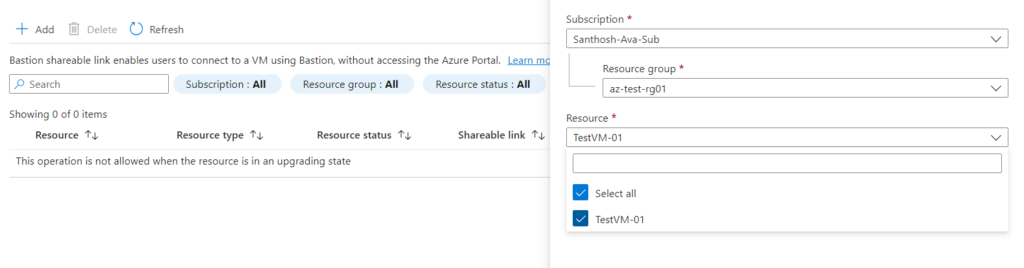
5. In the Create shareable link page, select the resources for which you want to create a shareable link. You can choose specific resources, or you can select all. A separate shareable link will be created for each selected resource. In my demo environment, I have chosen my test VM.
6. Each resource has its link. To share a link, copy it and send it to the intended user. It is important to note that the link does not include authentication credentials. The user who accessed the link to connect to the target resource should provide the appropriate credentials.
I hope you had a good time understanding the share link feature in Azure Bastion. That’s the end of our discussion.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

