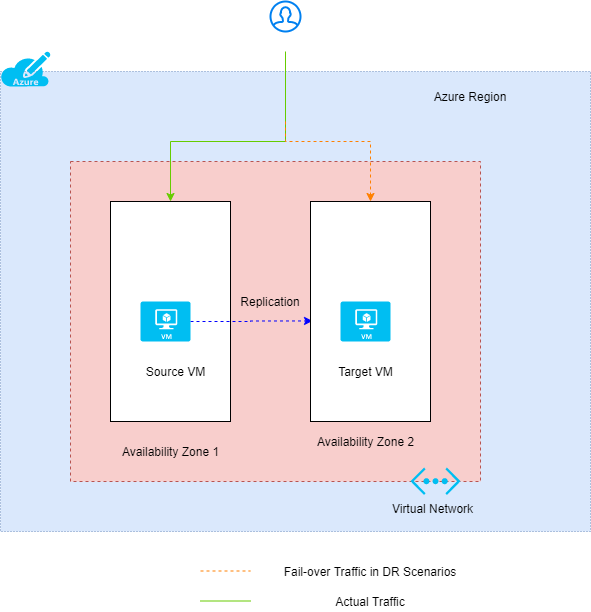
Azure Site Recovery contributes to an organisations business continuity and disaster recovery strategy by replicating workloads to secondary region. Microsoft announced Azure Site Recovery support for Zone to Zone disaster recovery in May 2020, which is currently available in limited with two regions: Southeast Asia and UK South (at the time of writing this article). This feature enables, replicate, failover, and failback Azure virtual machines from one Availability Zone to another within the same Azure region.This benefits organisations by managing disaster recovery solutions in a much simpler way and with minimal cost.
Availability Zones are physically separate locations within an Azure region. Each Availability Zone is made up of one or more data centers equipped with independent power, cooling, and networking.
Benefits & Disadvantages
- This solution will be useful for organisation who look to build a Disaster Recovery strategy within the same metro region.
- In some Azure regions where it does not have geographically-paired regions, this solution can serve as a disaster recovery component mainly concerned with GDPR and legal jurisdiction.
- The Zone to zone disaster recovery feature reduces network complexity for the organisation who has a complex networking infrastructure and who don’t want to have a same setup in another region. This will have cost-benefit too.
- At the same time it has disadvantages, in the event of a total region failure due to natural disaster, Zone to Zone will not allow a recovery option from another region (secondary) for business continuity and Diaster recovery purpose.
Networking requirements Zone to Zone Disaster Recovery:
Let’s discuss the networking component involved in this solution:
- Virtual network: We can use the same virtual network across zones in a region for a failover scenario. This provides a simpler way of network management. As typically the best practice Azure Site Recovery failover is to use different virtual networks.
- Subnet: Failover into the same subnet in the same virtual network or different subnet on other virtual network.
- Private IP address: we can assign the same static IP address in target Zone, if we choose to configure.
- Public IP address: We can attach a previously created Standard Public IP to a target VM. The Basic SKU version is not supported.
- Load balancer: Standard Load balancer supports to add a target zone VM to the same backend pool.
- Network Security Group: Re-use the same Network Security Group as a source VM.
Assumptions:
- You need to have valid subscriptions in Azure.
- The reader knows about creating Azure resources (Virtual machine, network).
- Provisioning the mentioned resources will have cost on your subscription.
Working setup:
Since at the time of publishing this blog, the service is currently available in South East Asia (Singapore) region, all resources will be deployed to it.
In this setup, we will provision the below resources in the same region (Azure South East Asia):
- Two Azure Resource groups for the source VM and target VM replication. Since failover should be in a different resource group and same resource group is not supported since workloads name will be similar).
- Two virtual networks, one for actual workload and the other for testing failovers.
- One Windows virtual machine placed in the Availability Zone.
- Azure Site Recovery for replication of virtual machine.
Let’s get rolling with the deployment.
Azure VNET, resource group and virtual machine configuration:
In this section, we will create source virtual machines, virtual networks, and resource groups for the testing.
- Login to Azure portal and select resource groups from the home page, click “Add” at top of page.
- Select your desire Azure subscription and provide the name as “Azure-demo” for resource group and select South East Asia region. This resource group will be a source resource group.
- Click review + create and once validation passed click create.
- Repeat the above steps for creating a target resource group with the name “azure-dr-demo”.
- From the Azure portal home page, select “azure-demo” resource group. Click networkingà virtual network and fill the required details:
Subscription: Select your desired subscription
Resource group: select “Azure-demo”, which created for source resources.
Name: provide “azure-demo-vnet”
Location: South East Asia.
- Click next and provide IP address space:172.16.0.0/24.
- Select subnet and add provide subnet name “workload” and provide subnet range as “172.16.0.0/24 “.
- Leave others as default and Click review + create and once validation passed click create.
- Repeat steps 5 to 8 for creating another virtual network in resource group “azure-dr-demo”. Provide IP address space: 10.10.10.0/24.
- Create a source VM in the “Azure-demo” resource group and “Azure-demo-vnet” Virtual network.
- From the Azure portal home page, select “Azure-demo” resource group. Click the computerà virtual machine and fill the required details:
Subscription: Select your desired subscription
Resource group: select “Azure-demo”, which created for source resources.
Name: provide “azure-demo-vm01”
Location: South East Asia.
Availability options: Availability zone & zone 1
Image: Windows server 2016 datacentre.
Administrator account: Enter username
Administrator password: enter your password & re-confirm. Please note down credentials for later use.
Public inbound ports: allow selected ports. Select HTTP (80) & RDP (3389).
Note: Enabling RDP & HTTP from the public IP address is not recommended for production workloads.
- Click next: disks, keep defaults.
- Click next: networking.
Virtual network: Azure-demo-vnet
Subnet: workload
Public IP: create new. Enter a name and select Standard. It will be zone- redundant.
NIC NSG: Basic
Public inbound ports: allow selected ports. Select HTTP (80) & RDP (3389).
- Click next: management. I will turn off diagnostics and auto-shutdown for my testing workloads.
- Click Review + create and once validation passed click create.
Configure IIS on the virtual machine:
In this section, let install IIS and create a simple web site for accessing from the server. This will be used for testing Virtual machine after failover to another zone.
- Login to the created virtual machine by RDP with public IP and provide appropriate credentials.
- Run below command in PowerShell for installing IIS. Install-WindowsFeature -name Web-Server -IncludeManagementTools.
- Locate C:\inetpub folder and replace the content of iisstart.html file as below:
<header><title>Azure Page</title></header>
Welcome to Azure Site recovery zone to zone replication-demo.
4. Now, browse to the public IP address of the virtual machine in an internet browser and you should see the web page “Welcome to Azure Site recovery zone to zone replication -demo.”
Enable replication on a virtual machine to another zone:
In this section, we will create Azure site recovery and configure replication of the Virtual machine.
- From the Azure portal, click create the resource and search for Azure site recovery, select Backup, and site recovery. Click create.
- Provide the name (asr-test) and the select region as Azure South East Asia.
- Click Review + create and once validation passed click create.
- Go to the site recovery vault which we created on the above step. Click +replicate.
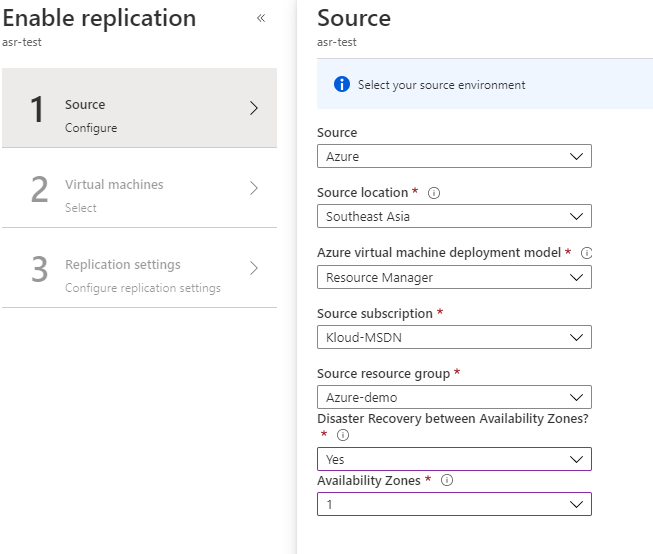
- Fill source details as below and click OK to save the details.
Source: Azure
Source location: South East Asia.
Source resource group: Azure-demo
Disaster Recovery between Availability Zones: yes.
Availability Zones: 1 (where the source virtual machine is provisioned)
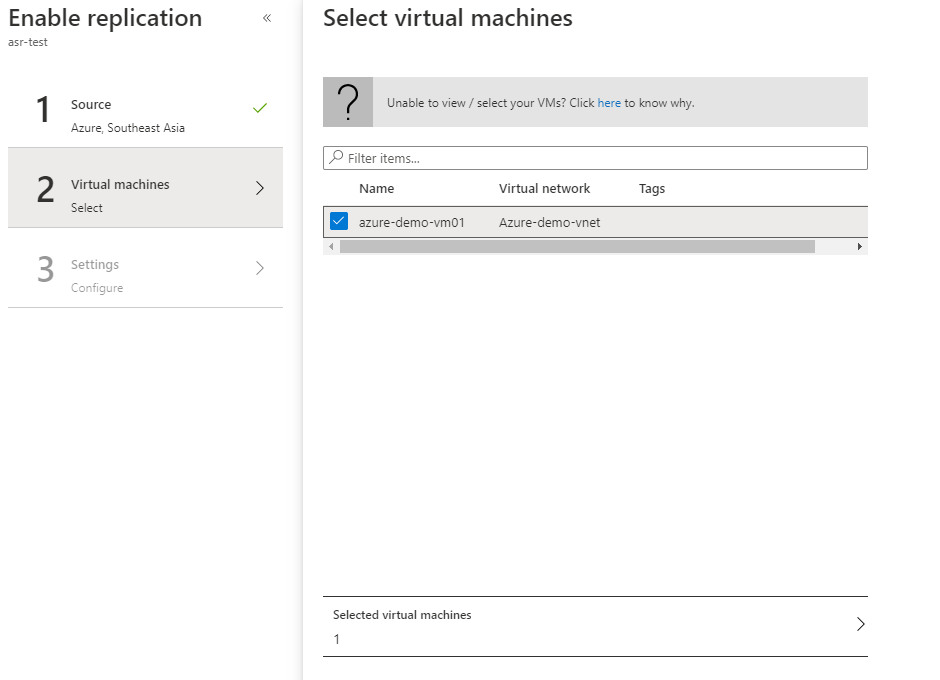
- Select the virtual machine and click OK.
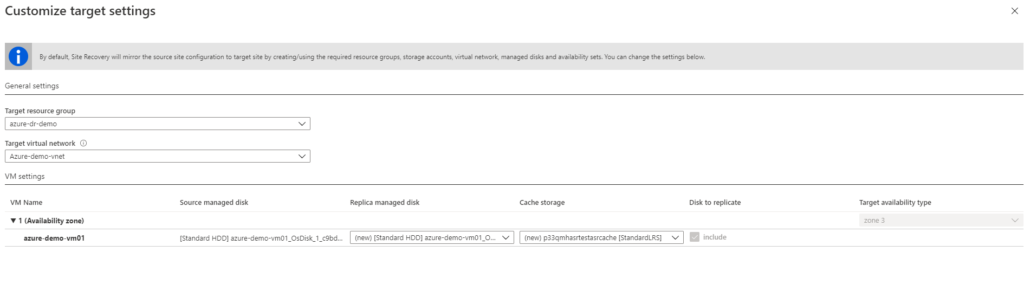
- Configure replication settings
Availability zones: 3 (Azure provides zones other than source VM is provisioned).
- Click customize to change target settings and click OK to save.
Target resource group: Azure-dr-demo
Target virtual network: demo-test-vnet01
Azure creates a storage account for replicating Virtual machine disks to the target site. Azure defaults create it, or you can specify your storage account. This will be in a source resource group.
If you want to change disk SKU to premium or standard for target VM can be performed on this page.
- Click customize next to the replication policy to change as per your requirements.
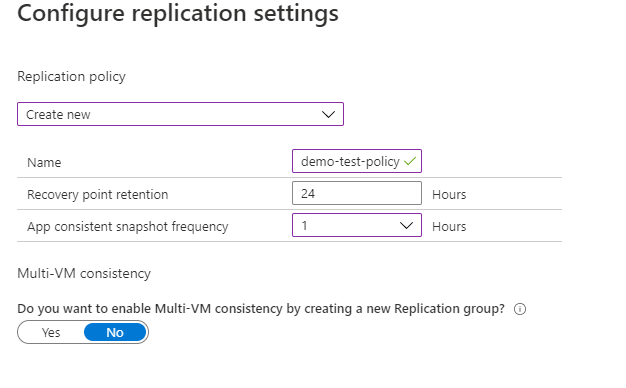
- Finally, click create target resources.
- Click enable replication. Initial replication will take a few minutes.
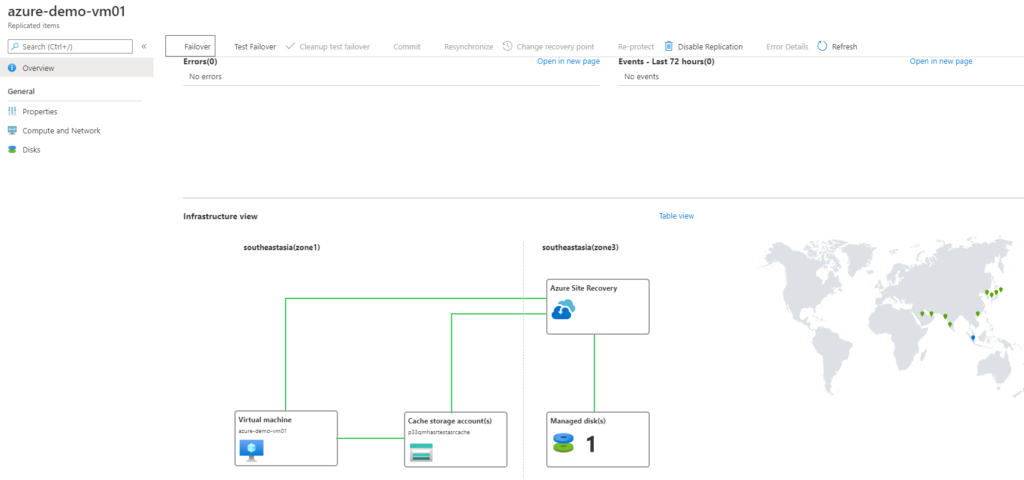
- After replication has completed, select Source VM and click on disaster recovery under operations. This picture gives clear information about replication.
Test Failover virtual machine to the secondary zone:
In this section, we will be performing a test failover procedure.
- From the Azure portal, select source virtual machine and click disaster recovery under operations. The same step can be performed from the vault, replicated items.
- Click test failover and select recovery points from options and test virtual networks.
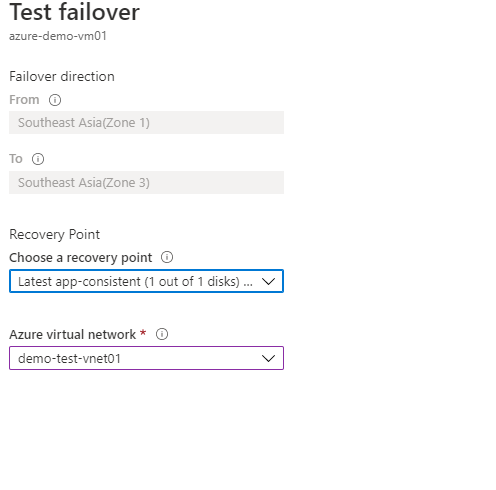
- Click OK.
- To check the progress, go back to the vault, select site recovery jobs.
- After failover finishes, virtual machines will appear in the test resource group. Ensure the virtual machine is created in an appropriate availability zone (in my test case it will be 3), connected to test network and size. To check the consistency of application, create a new public IP address to test virtual machine.
- After verification, on the virtual machine click to clean up test failover.
Actual Failover of a virtual machine to a secondary zone:
In this section, we will be performing an actual failover procedure.
- From the Azure portal, select source virtual machine and click disaster recovery under operations. The same step can be performed from the vault, replicated items.
- Click failover and select recovery point from options: latest.
- Select the shutdown machine before beginning Failover. This will ensure no data loss. Even if shutdown fails, failover will occur. Click OK.
- To check the progress, go back to the vault, select site recovery jobs.
- After failover is complete, select target resource group and view the virtual machine is provisioned with zone 3 (secondary).
- To ensure having the same public IP address, disassociate existing public IP address from source virtual machine and associate to target (replicated) virtual machine.
- You can assign source VM NSG to target (replicated) virtual machine. If you have NSG at the subnet level and happy with it.
- Login to target virtual machine with a public IP address and verify the server by providing localhost on VM browser and could see the web page “Welcome to Azure Site recovery zone to zone replication -demo.”
- place the public IP address of the virtual machine on a browser and could see the web page “Welcome to Azure Site recovery zone to zone replication -demo.”
- After verifying the server and satisfied with the failed over a virtual machine, you can Commit the failover. You can use a change recovery point to change different recovery options for VM. Once committed, cannot change the recovery point.
Re-protect virtual machine to the primary zone:
- After failover committed, re-protect VM to the primary zone (when the primary zone is available). Failback will available only after re-protect is enabled.
- From Vault, select replicated items and click on VM and select Re-protect.
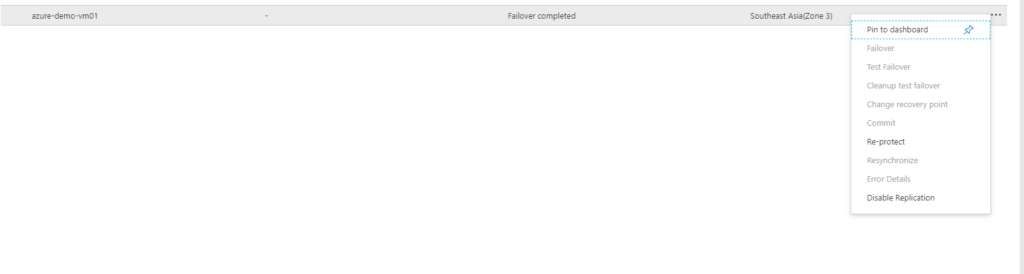
- Verify the settings of replication to primary zone resources and click OK.
- Wait till re-protect is completed for performing the fail-back of a virtual machine to the primary zone.
Failback virtual machine to the primary zone:
- From Vault, select replicated items and click on VM and select failover.
- Select recovery point from options: latest
- Select the shutdown machine before beginning Failover. This will ensure no data loss. Even if shutdown fails, failover will occur.
- It might give warning as test failover has not performed, accept a risk, and Click OK.
- To check the progress, go back to the vault, select site recovery jobs.
- After the failover is complete, select the target resource group and view the virtual machine is provisioned with zone 1 (primary).
- To ensure having the same public IP address, disassociate existing public IP address from target virtual machine and associate to source virtual machine in the primary zone.
- Login to source virtual machine with a public IP address and verify the server by providing localhost on VM browser and could see the web page “Welcome to Azure Site recovery zone to zone replication -demo.”
- place the public IP address of the virtual machine on a browser and could see the web page “Welcome to Azure Site recovery zone to zone replication -demo.”
- After verifying the server and satisfied with the failed over a virtual machine, you can Commit the failover. You can use a change recovery point to change different recovery options for VM. Once committed, cannot change the recovery point.
- Finally, enable re-protect for source virtual machine to a secondary zone for protection.
Things to note:
- Zone to zone Disaster recovery supported only in UK south and South East Asia.
- Recovery plans for Zone to Zone disaster recovery via the portal are not supported and use PowerShell and REST API.
- Occasionally virtual machines behind a public load balancer, will show config error and it would not stop virtual machine replication.
- If workloads require Azure load balancer, then ensure you have a zone redundant load balancer is created. You can proceed with the same procedure for replication. After failover, add the new target virtual machine into a load balancer backend pool.
- For machines running the Site Recovery extension version 9.28.x.x onwards Update rollup 40 Site Recovery cleans up machines in the secondary disaster recovery region after failback is complete and VMs are re-protected. There is no need to manually delete VMs and NICs in the secondary region. If you completely disable replication after failing back, Site Recovery cleans up the disks in the disaster recovery region, in addition to the VMs and NICs.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

