Azure Cloud provides a variety of networking capabilities that can be used together or separately to meet different customer requirements. Utilize the Azure Application delivery services to ensure the application is secure and safe.
Azure provides four types of networking services:
Connectivity Services: Integrate Azure and On-premise resources using one or more services in Azure. Services: Azure Vnet, Express route, Peering, Gateway.
Application Protection Services: Protecting applications hosted in Azure cloud using any or a combination of the services in Azure. Services: Firewall, NSG, WAF, and Azure Private link.
Application Delivery Services: Delivering the application hosted in Azure to end customers by using any or a combination of the services in Azure. Services: Application gateway, CDN, traffic manager, Azure front door, and Load balancer
Networking Monitoring: Monitor the health of Azure networking services using one or a combination of services in Azure. Services: Network watcher, Azure monitor.
In this blog post series, I walk through different networking application delivery services with features and limitations on each service. In the first part of the networking series, let’s discuss Azure Load Balancer and its features.
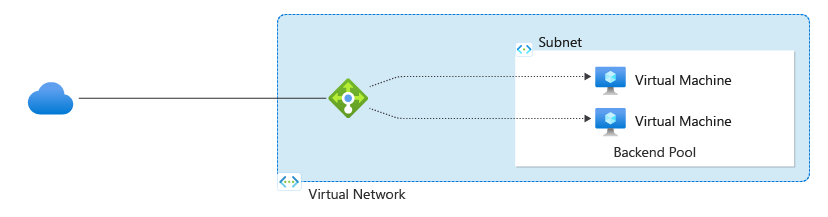
Azure Load Balancer
- This evenly distributes the network traffic from the Frontend to two or more Backend servers or resources.
- This service operates at layer 4 of the OSI model and routes traffic based on a source IP address and port to a destination IP address and port.
- A Health probe determines the health status of instances in the backend servers (Pool) and route traffic based on it.
- A Load balancing rule defines how incoming traffic is distributed to instances within the backend pool.
- Azure Load Balancer supports availability zone types. Create a Standard Load Balancer to increase availability throughout the scenario by aligning resources with and distribution across zones.
- A Load Balancer can either be zone redundant, zonal, or non-zonal. Select the appropriate type of frontend needed to configure the zone-related properties for the load balancer.
- Azure provides different SKU types of load balancers:
- Basic Load Balancer (retires sooner)
- Standard Load Balancer
- Gateway Load Balancer
- Cross-Region Load Balancer (Preview)

Basic LB: Basic tier load balancer provides basic features and is restricted to some limits for backend pool size. It is restricted to only 300 instances, it’s bound to a single availability set, and it only supports multiple frontends for inbound traffic. On September 30, 2025, Basic Load Balancer will be retired. For more information, see the official announcement.
Standard LB: Standard tier load balancer is generally available and offers higher-scale and new features. It is a paid-for feature using a complex set of consumption-based charges. Also, we can scale out to 1000 instances and span any virtual machine in a single virtual network, including blends of scale sets, availability sets, and appliances. Standard Load Balancer routes traffic within availability zones for high resiliency.
Standard Load Balancer offers zone redundancy; it is a regional resource. If a regional outage occurs, causing the Load Balancer or all the backend servers to go unavailable, traffic will not be able to be forwarded as it arrives at the Load Balancer frontend.
Please visit the official site to learn the difference between Basic and Standard SKUs.
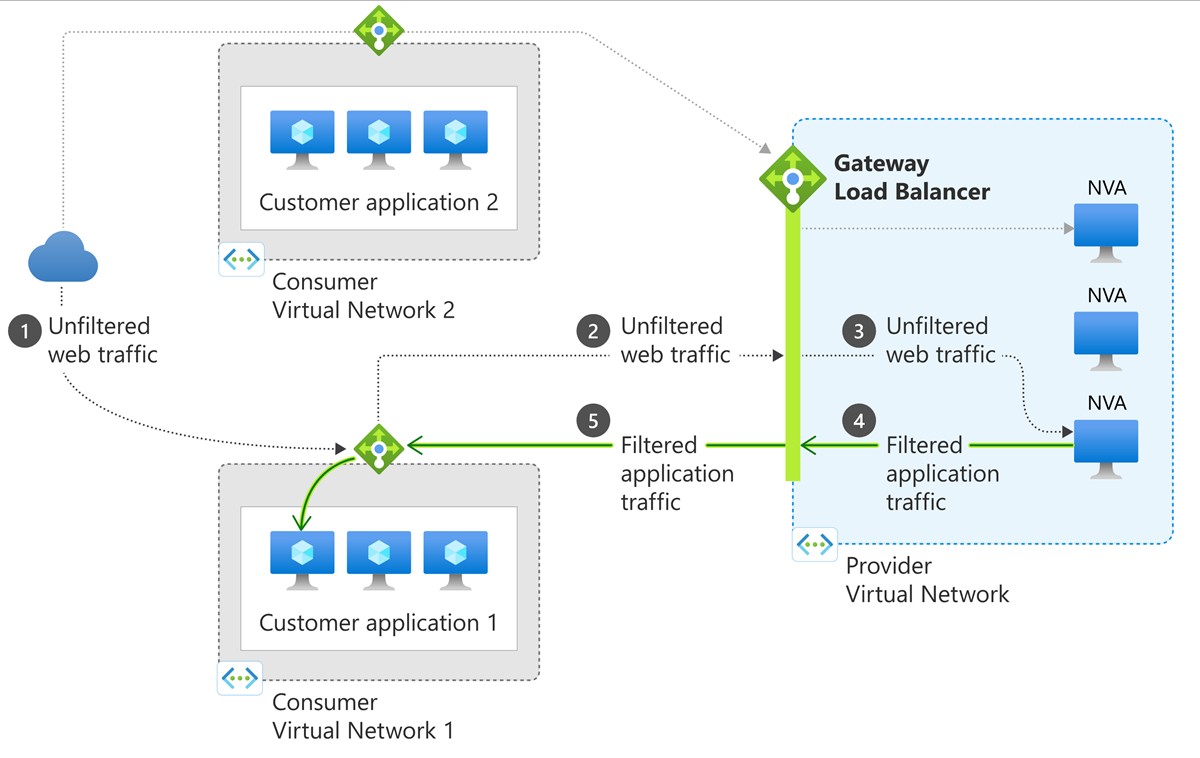
Azure Gateway Load Balancer:
Gateway Load Balancer is a fully managed service enabling you to deploy, scale, and enhance the availability of third-party NVAs in Azure. With the capabilities of Gateway LB, You can add your favorite third-party appliance, whether a firewall, inline DDoS appliance, deep packet inspection system, or even custom appliance, into the network path transparently.
With Gateway Load Balancer, you can easily add or remove advanced network functionality without additional management overhead. You can think of Gateway LB as providing the bump-in-the-wire technology to ensure all traffic to a public endpoint is first sent to the appliance before your application. Gateway LB is even more powerful by ensuring symmetrical flows or a consistent route to your network virtual appliance – without manually updating routes. As a result, packets traverse the same network path in both directions to function can do so.
Gateway Load Balancer combines a pass-through load balancer to distribute your traffic at scale and a single entry and exit point for your traffic – with a single click. All you need to do is chain your application to a Gateway Load Balancer. You can scale up or scale down as needed. You can also leverage auto-scale with virtual machine scale sets. You can insert appliances transparent for different kinds of scenarios, such as:
- Firewalls
- Advanced packet analytics
- Intrusion detection and prevention systems
- Traffic mirroring
- DDoS protection
- Custom appliances
Gateway LB limitations, at the moment of writing:
- Gateway Load Balancer doesn’t currently support IPv6
- Does not support the global load balancer tier.
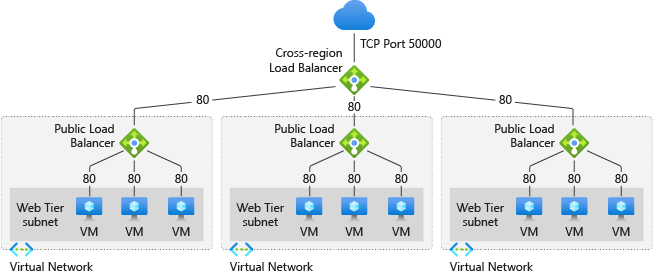
Cross-Region Load Balancer
Azure’s cross-region Load Balancer has a single unique globally anycast IP to load balance across the Azure regions. Azure’s cross-region Load Balancer distributes traffic to the closest region, ensuring low latency when using the service.
By incorporating Azure Cross-region Load Balancer into end-to-end architecture, the customers can achieve region redundancy, high availability, and low latency for their end applications with a quick turnaround time for scaling events while retaining their IPs for TCP and UDP connections.
If one region fails, the traffic is routed to the next closest healthy regional load balancer. The health probe of the cross-region load balancer gathers information about the availability of each regional load balancer every 20 seconds. If one regional load balancer drops its availability to 0, the cross-region load balancer will detect the failure. The regional load balancer is then taken out of rotation.
Cross-Region LB limitations, at the moment of writing:
- An internal frontend is not supported, and public IP configurations are not supported.
- UDP traffic isn’t supported on Cross-region Load Balancer.
- Private or internal load balancers can’t be added to the backend pool of a cross-region load balancer.
The next part of this blog will cover traffic manager, Application gateway, and Azure Front door services.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

