Welcome to my blog! In this post, I will give you a comprehensive overview of Azure Network Security Perimeter (NSP) services. Announced at last year’s MS Ignite and recently made generally available, this service offers unique features that distinguish it from other options. Let’s explore its key attributes and understand their significance in enhancing Azure PaaS network security.
Understanding the Network Security Perimeter
Azure’s Network Security Perimeter (NSP) is a service designed to provide centralised security and governance for Azure Platform as a Service (PaaS) inbound and outbound connectivity, which has a public endpoint. It primarily targets PaaS services that operate through public endpoints, where PaaS provides both inbound and outbound access via a public IP address.
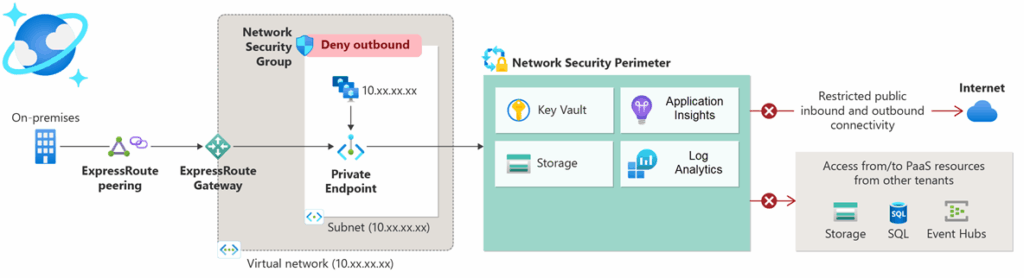
The Azure Network Security Perimeter creates logical boundaries around PaaS resources outside your virtual networks, helping to regulate public access to services like Azure Storage accounts and Azure Key Vault. By default, it restricts public access; however, you can create specific access rules for both inbound and outbound traffic. This setup protects against data exfiltration while ensuring necessary connectivity for your applications.
What problem does NSP solve?
Azure offers a variety of Platform as a Service (PaaS) options and includes several methods for restricting access to these services. Key features include service endpoints, private endpoints, and IP whitelisting. However, the NSP provides distinct advantages that differentiate it from these other options:
- NSP enables more effective restriction on outbound traffic for PaaS services, an area where alternative solutions are often limited.
- NSP offers a centralised management interface for governing both inbound and outbound access restrictions for all Azure PaaS services.
- NSP includes scaling options that enhance the ability to restrict access to Azure PaaS services as needed.
Key Components of Azure Network Security Perimeter
A network security perimeter architecture encompasses the following components:
- Network Security Perimeter: This is a top-level resource that defines the logical network boundary for securing Platform as a Service (PaaS) resources.
- Profile: This refers to a collection of access rules that apply to resources associated with the profile.
- Access Rule: These are the inbound and outbound rules for resources within a perimeter that facilitate access beyond the perimeter.
- Resource Association: This denotes the perimeter membership of a PaaS resource.
- Diagnostics Settings: This feature helps collect logs and metrics for all resources within the perimeter.
The Role of Azure Network Security Perimeter
Let’s discuss the role of NSP and how it differs from other services. Azure offers private endpoints for almost every Azure PaaS service, enabling a secure connection through a NIC attached to an Azure virtual network. This allows for a fully private connection without traversing the Internet. While using private endpoints is a best practice, there are some scenarios where we need to use public endpoint access to integrate with third-party services that require it.
Another option for managing PaaS service public endpoints is specifying allowed networks and IP addresses. However, this must be set up for each resource, creating overhead for larger environments.
To address the above-mentioned points, Network Security Perimeter enables centralised policy creation and management, ensuring consistent security enforcement across your environment.
NSP can restrict PaaS resources with two different associations that can be set:
Enforced mode – This mode must be set by an administrator. In this mode, all traffic is blocked by default, except for traffic within the perimeter, unless an Allow access rule is in place.
Transition mode (formerly Learning mode) – This is the default mode. It helps network administrators see how PaaS resources are being accessed. It is recommended to use this mode before switching to enforced mode.
The service is currently generally available. For more information on current limitations, please visit the Microsoft page.
Implementing Azure Network Security Perimeter
Let me show you, with an Azure storage resource, how to restrict access by NSP features. As a prerequisite, create an Azure storage account within your subscription and let’s start creating the NSP resource now.
- Log in to the Azure portal with the required credentials.
- Search for network security perimeters and select them. In the network security perimeters window, select + Create.
- Provide the required information for creating NSP services, such as Name, Resource group, location and Profile name.
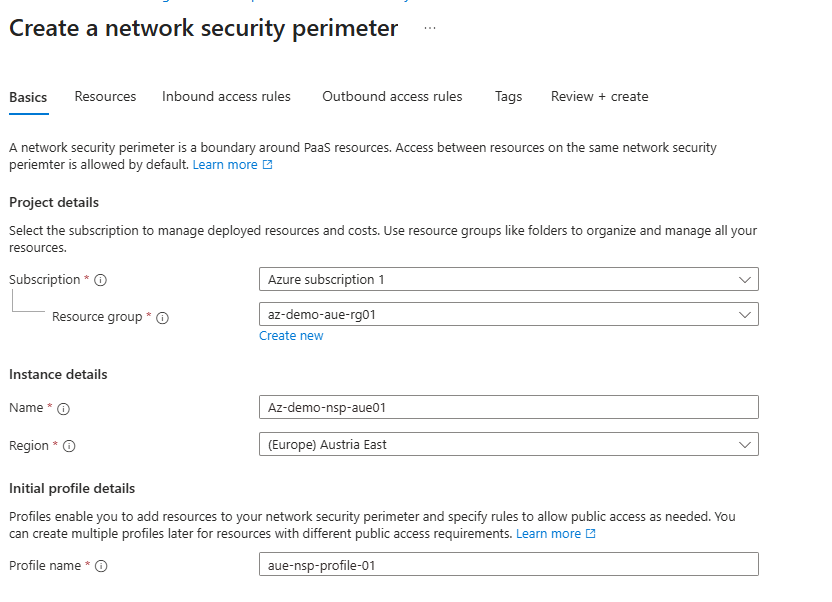
- Click Next.
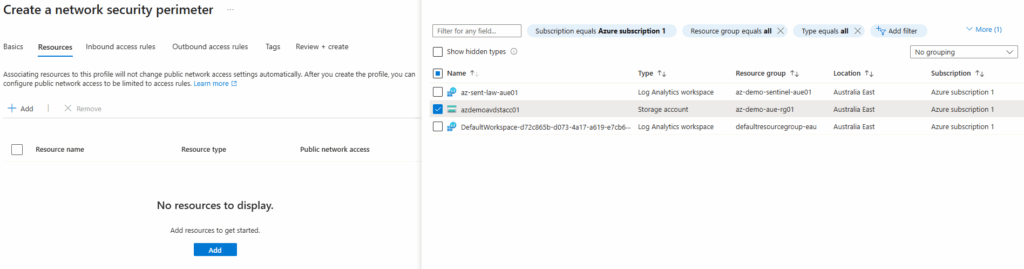
- In the Resources tab, select + Add. Select the Azure storage PaaS resource that we have created earlier and choose Select.
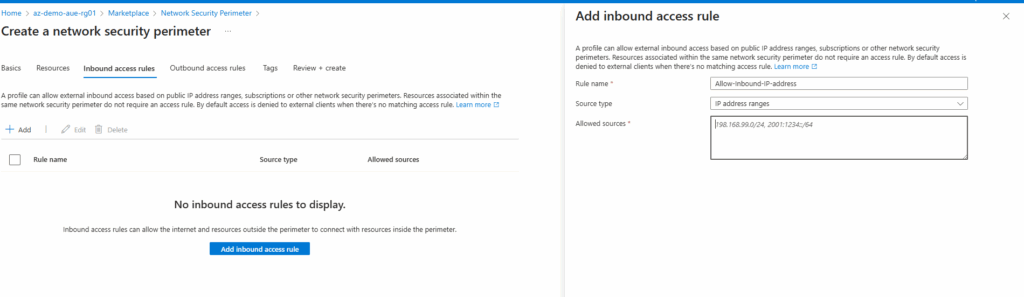
- In the next section, ‘Inbound Access Rules,’ select ‘+’ Add. In the Add inbound access rule window, enter the rule name, source type and source information and select Add:
- For my testing, I will add my public IP address, formatted xx.xx.xx.xx/32 (/32 for a single IP address), to the source for testing inbound access to the storage account.
- For this testing purpose, I will leave the default for the outbound access rule and click Next.
- Select Review + create and then Create. Select Go to resource to view the newly created network security perimeter.
Testing the Scenarios
- By default, the access mode is Transition, and it does not block the public endpoint access if the resources are enabled.
- We need to change to Enforced mode: By default, all traffic except intra-perimeter traffic is denied in this mode unless an Allow access rule exists.
- Select the Profile in the NSP resource and click on the associated resource to view the access mode.
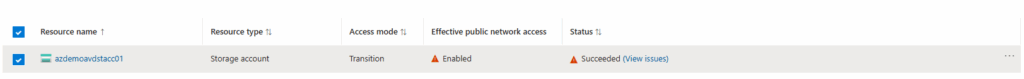
- To change the access mode, click the three dots on the profile and select the desired access tier mode. Select Enforced access mode.
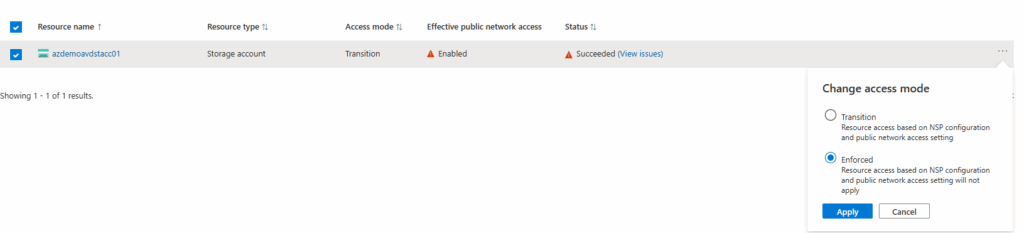
- Click Apply.
- After applying the rule, access the browser to view the blob or container. I can access the blob.
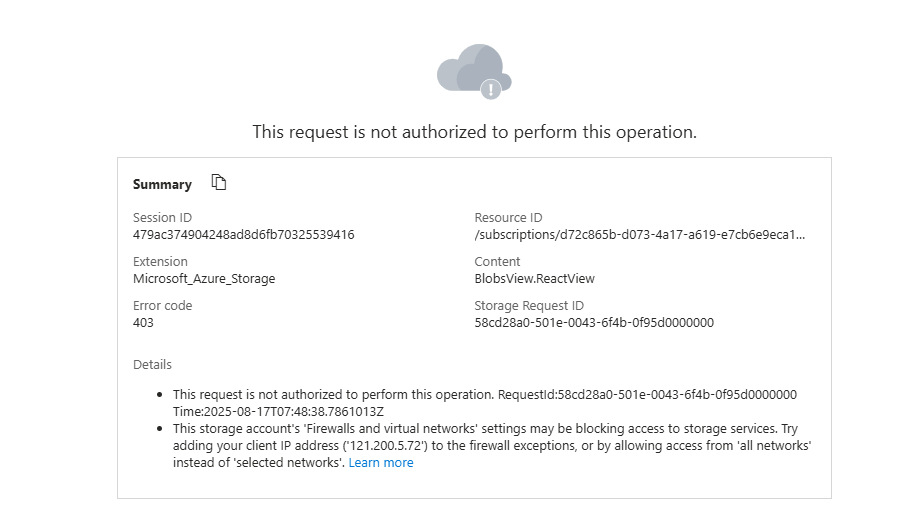
- To confirm that the NSP testing is working, I was denied access when attempting to access it from another IP address.
Conclusion: Strengthening Your Azure PaaS Security Posture
In conclusion, utilising network security perimeter services is essential for safeguarding Azure PaaS resources. By establishing a secure boundary, organisations can effectively prevent data leakage while maintaining control over access rules and ensuring compliance with audit requirements. This approach not only enhances security but also simplifies management through centralised oversight. Embracing these services allows businesses to confidently deploy and scale their applications while protecting critical data from potential threats.

Santhosh has over 15 years of experience in the IT organization. Working as a Cloud Infrastructure Architect and has a wide range of expertise in Microsoft technologies, with a specialization in public & private cloud services for enterprise customers. My varied background includes work in cloud computing, virtualization, storage, networks, automation and DevOps.

